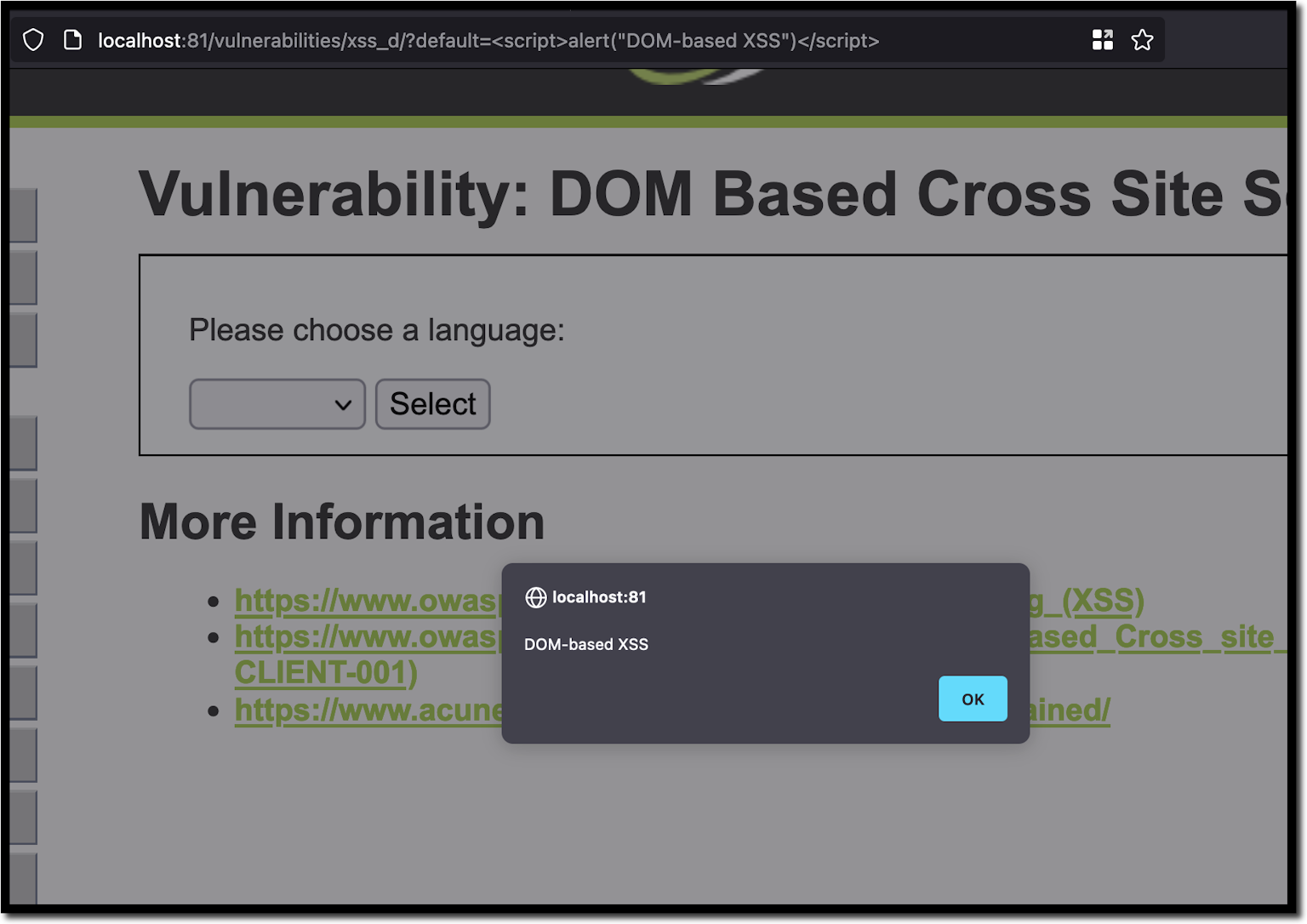
XSS by using onclick · Issue #8000 · Dolibarr/dolibarr · GitHub
Por um escritor misterioso
Descrição
Bug The xss filter in "htdocs/main.inc.php" is not enough, we can just use "onclick" and "onscroll" to bypass the filter,eg: <div style="position:absolute;top:0;left:0;width:100%;height:100%" onclick="alert(52)"> , <body onscroll=alert(1
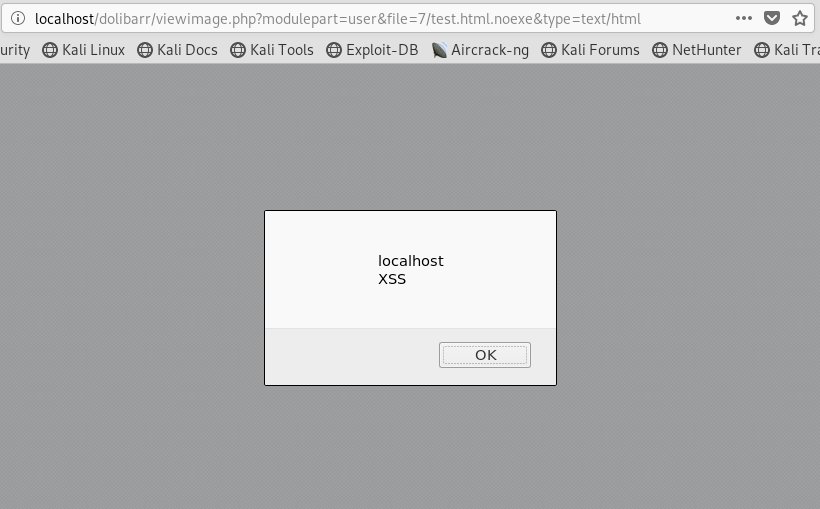
Dolibarr Version 9.0.1 — Multiple Vulnerabilities
GitHub - s0md3v/AwesomeXSS: Awesome XSS stuff
XSS by using onclick · Issue #8000 · Dolibarr/dolibarr · GitHub
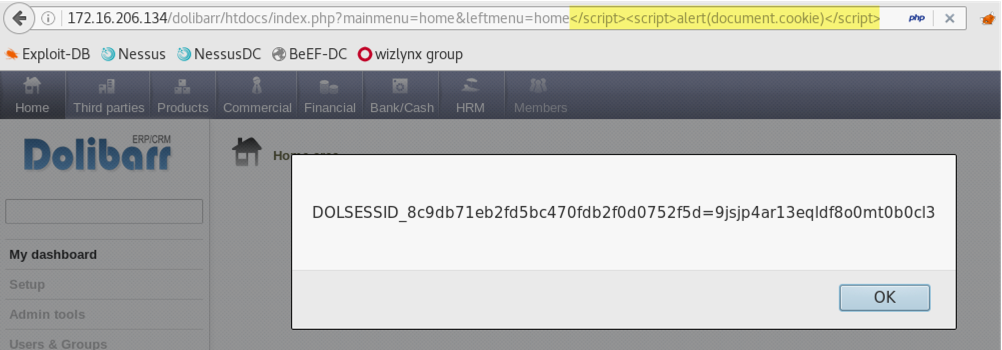
wizlynx group Multiple Reflected & Stored Cross-Site Scripting
GitHub - dxa4481/XSSJacking: Abusing Self-XSS and Clickjacking to
GitHub - kleiton0x00/XSScope: XSScope is one of the most powerful

Cross-site scripting (XSS) Attack using XSSER

65536 messages in process buffer, 100% utilized - Graylog Central
GitHub - kleiton0x00/XSScope: XSScope is one of the most powerful
GitHub - dogukankurnaz/XSS_Scanner: XSS Scanner Shell/Bash
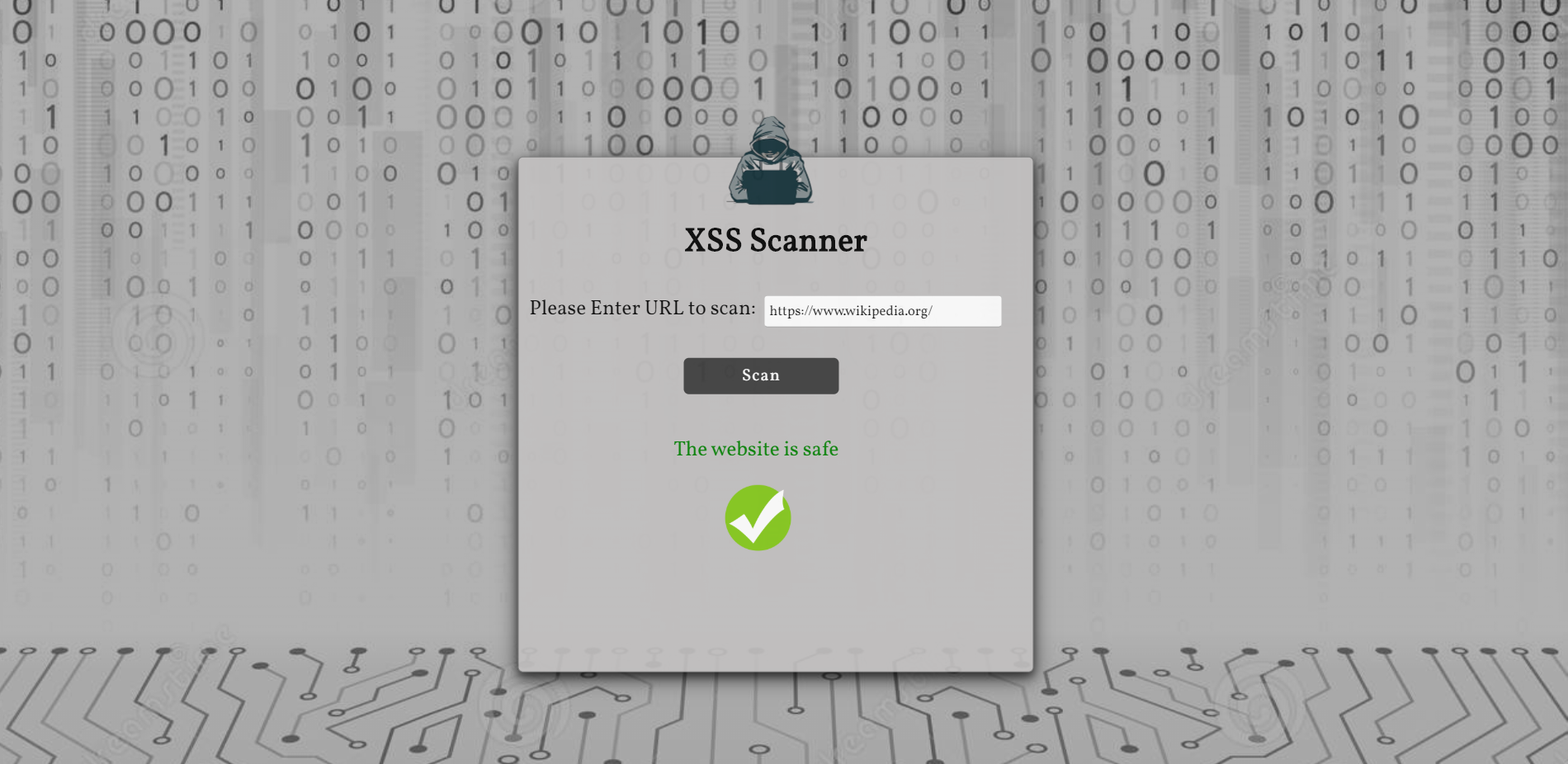
XSS-Scanner - XSS Scanner That Detects Cross-Site Scripting
de
por adulto (o preço varia de acordo com o tamanho do grupo)