Major surge in memory-based attacks as hackers evade traditional
Por um escritor misterioso
Descrição
Protecting workloads with tools that understand how to interpret attacks on cloud runtime environments is crucial.

Major surge in memory-based attacks as hackers evade traditional

How Hackers Use Social Engineering to Spread Dridex Malware

Code Obfuscation: A Comprehensive Guide Against Reverse

Has an AI Cyber Attack Happened Yet?

FUD Malware obfuscation engine BatCloak continues to evolve

How to Prevent Malware Attacks
Most Common Malware Attacks
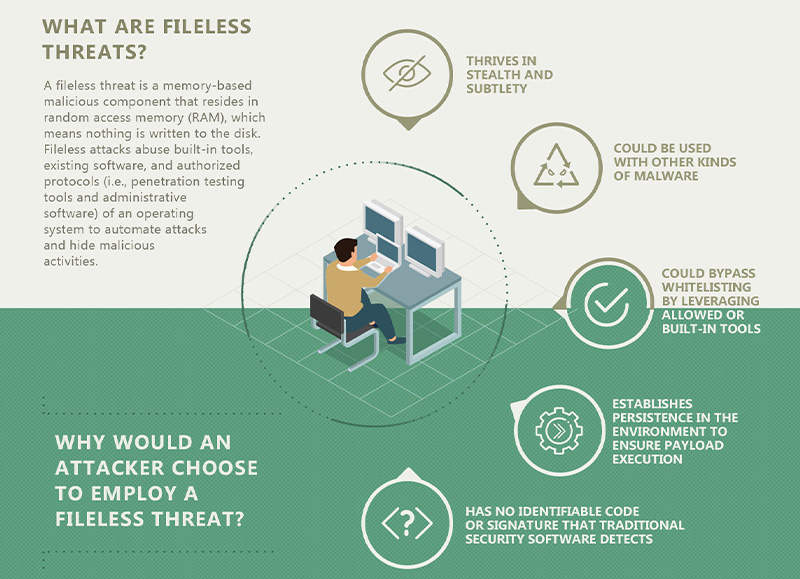
Security 101: How Fileless Attacks Work and Persist in Systems

Privilege Escalation Attack and Defense Explained

115 cybersecurity statistics + trends to know in 2024
“PACMAN” Hack Breaks Apple M1's Last Line of Defense - IEEE

Could Brute Force Attacks in a Post-Quantum Computing World Lessen
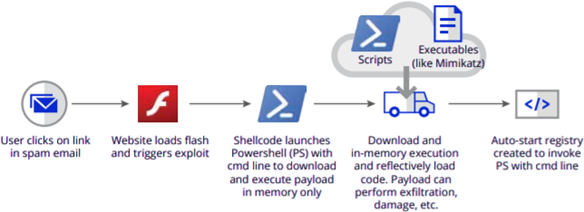
Fileless Malware Evades Detection-Based Security

Runtime Attacks In-Memory Require a Different Response
de
por adulto (o preço varia de acordo com o tamanho do grupo)