Cybercriminals turn Facebook's security features into exploits
Por um escritor misterioso
Descrição
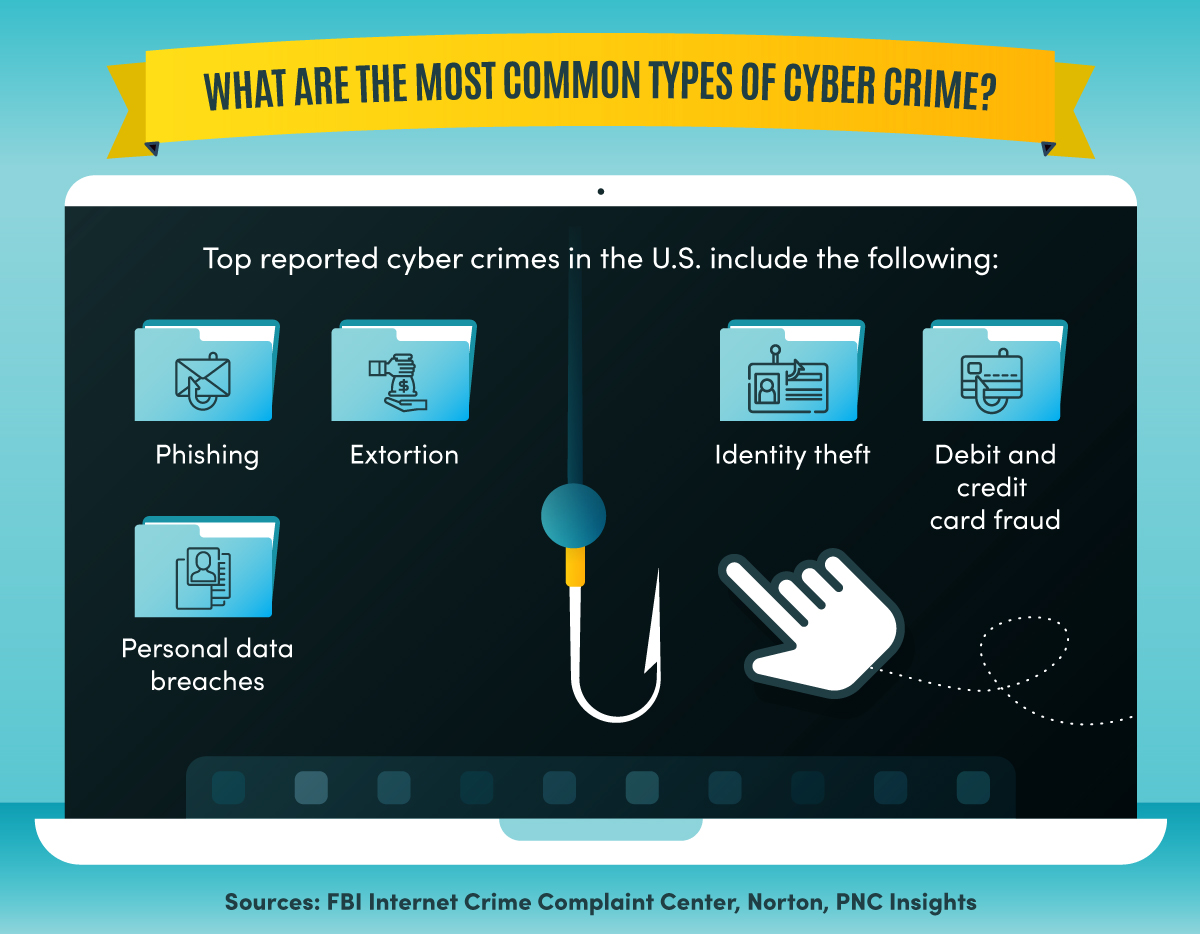
Cyber Crime Investigation: Making a Safer Internet Space

Exploiting AI: How Cybercriminals Misuse and Abuse AI and ML - Security News

The 15 biggest data breaches of the 21st century

Top 8 Vulnerable Cyber Security Risks

Cybercriminals Increasingly Using EvilProxy Phishing Kit to Target Executives

A new colour for your Facebook profile? It's a scam, Malware

10 Essential Steps to Fortify Your Facebook Account Security - Hongkiat
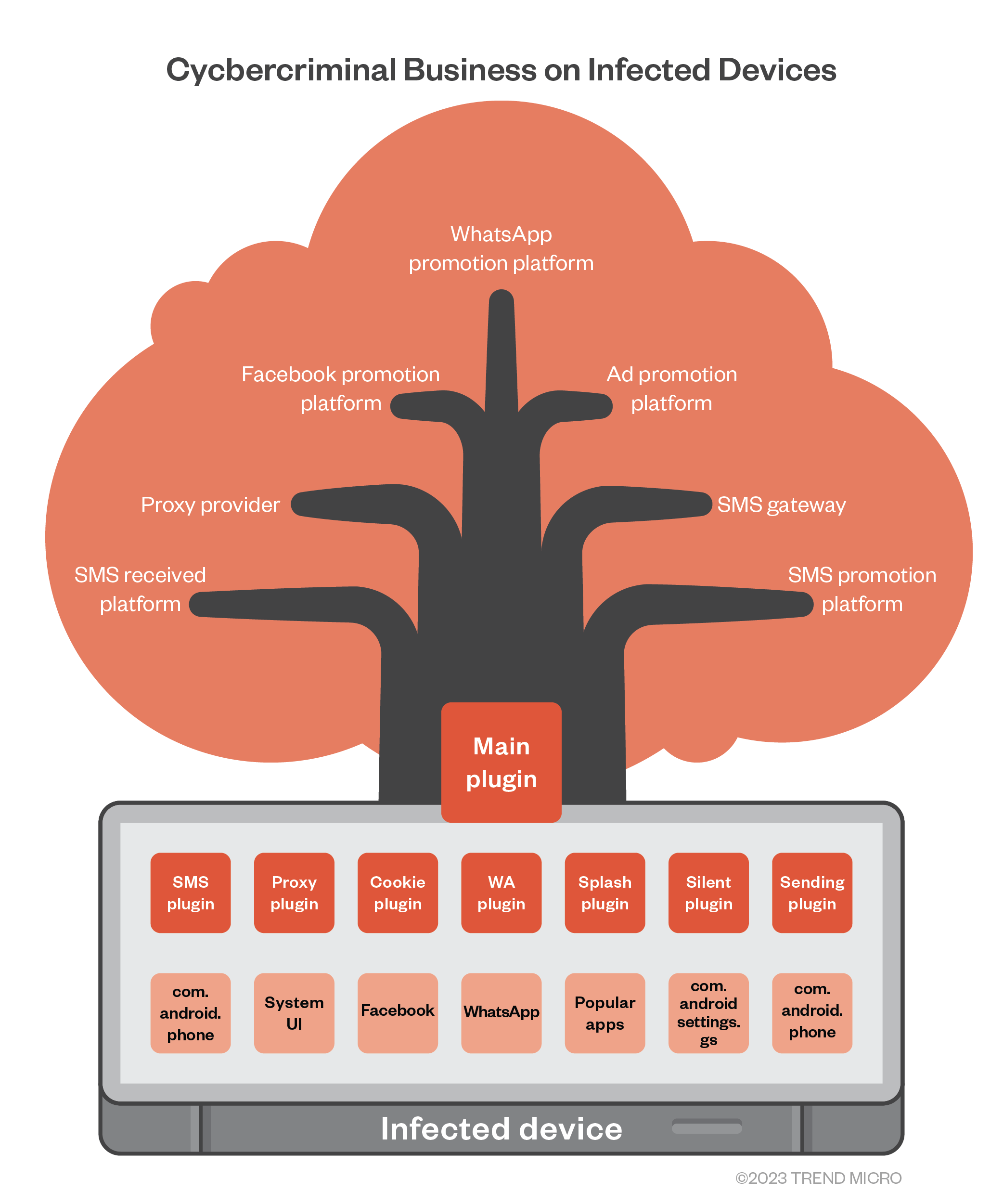
Lemon Group's Cybercriminal Businesses Built on Preinfected Devices

Zero-day in Salesforce email services exploited in targeted Facebook phishing campaign

Proxyjacking: The Latest Cybercriminal Side Hustle

Cybercriminals turn Facebook's security features into exploits

Vulnerabilities identified in the Abode IOTA security system: Fake image injection into timeline

PNG Department of Information and Communications Technology - CYBER SECURE AT WORK TIPS •Treat business information as personal information. Business information typically includes a mix of personal and proprietary data. While you
de
por adulto (o preço varia de acordo com o tamanho do grupo)