Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP
Por um escritor misterioso
Descrição

HoneyPi - An easy honeypot for a Raspberry Pi - TrustFoundry

Thoughts on the Application of Low-Interactive Honeypot Based on Raspberry Pi in Public Security Actual Combat, LIHRP

PART 1: LET'S CREATE A HONEYPOT FROM SCRATCH USING A #RASPBERRYPI #LIVEHACKING #LEARNTOLEARN

Testing a Low-Interaction Honeypot against Live Cyber Attackers
Installing DShield Honeypot on a Raspberry Pi, by Matt Kmety, The Startup

Low, Medium and High Interaction Honeypot Security

Enhancing Cybersecurity with Low-Interaction Honeypots: A Strategic Approach to Threat Intelligence
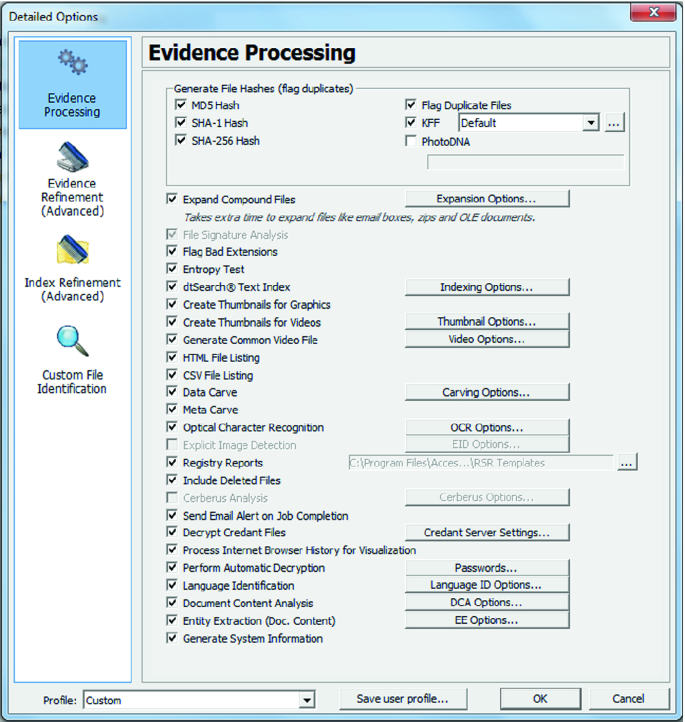
Digital Forensics of Raspberry Pi Used for MITM

Lightweight On-Demand Honeypot Deployment for Cyber Deception
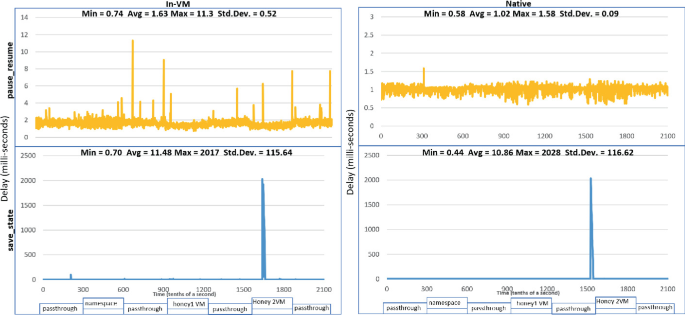
Lightweight On-Demand Honeypot Deployment for Cyber Deception

Enhancing Cybersecurity with Low-Interaction Honeypots: A Strategic Approach to Threat Intelligence
PDF) A Survey on Potential Applications of Honeypot Technology in Intrusion Detection Systems
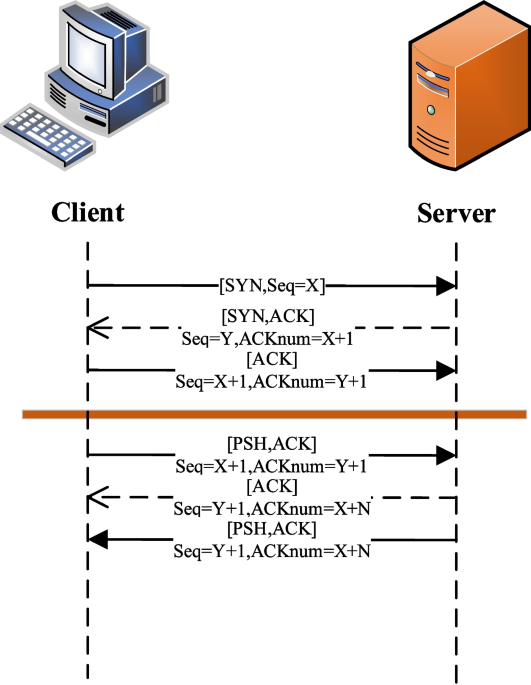
A new dynamic security defense system based on TCP_REPAIR and deep learning, Journal of Cloud Computing
de
por adulto (o preço varia de acordo com o tamanho do grupo)