Attackers use dynamic code loading to bypass Google Play store's
Por um escritor misterioso
Descrição
Threat actors rely on the 'versioning' technique to evade malware detections of malicious code uploaded to the Google Play Store
SharkBot: a “new” generation Android banking Trojan being

Banking Trojans sneaked into Google Play store disguised as apps

Appdome How to Use Appdome MOBILEBot™ Defense

Load data using a third-party application, BigQuery

Analysis of dynamic code updating in Android with security

SSL Pinning Bypass Android Using Frida
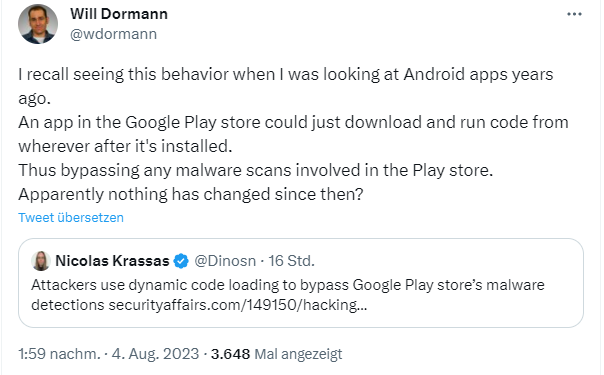
Bypass malware detection in Google Play Store with Dynamic Code

Threat actors abuse public cloud services to spread multiple RATs
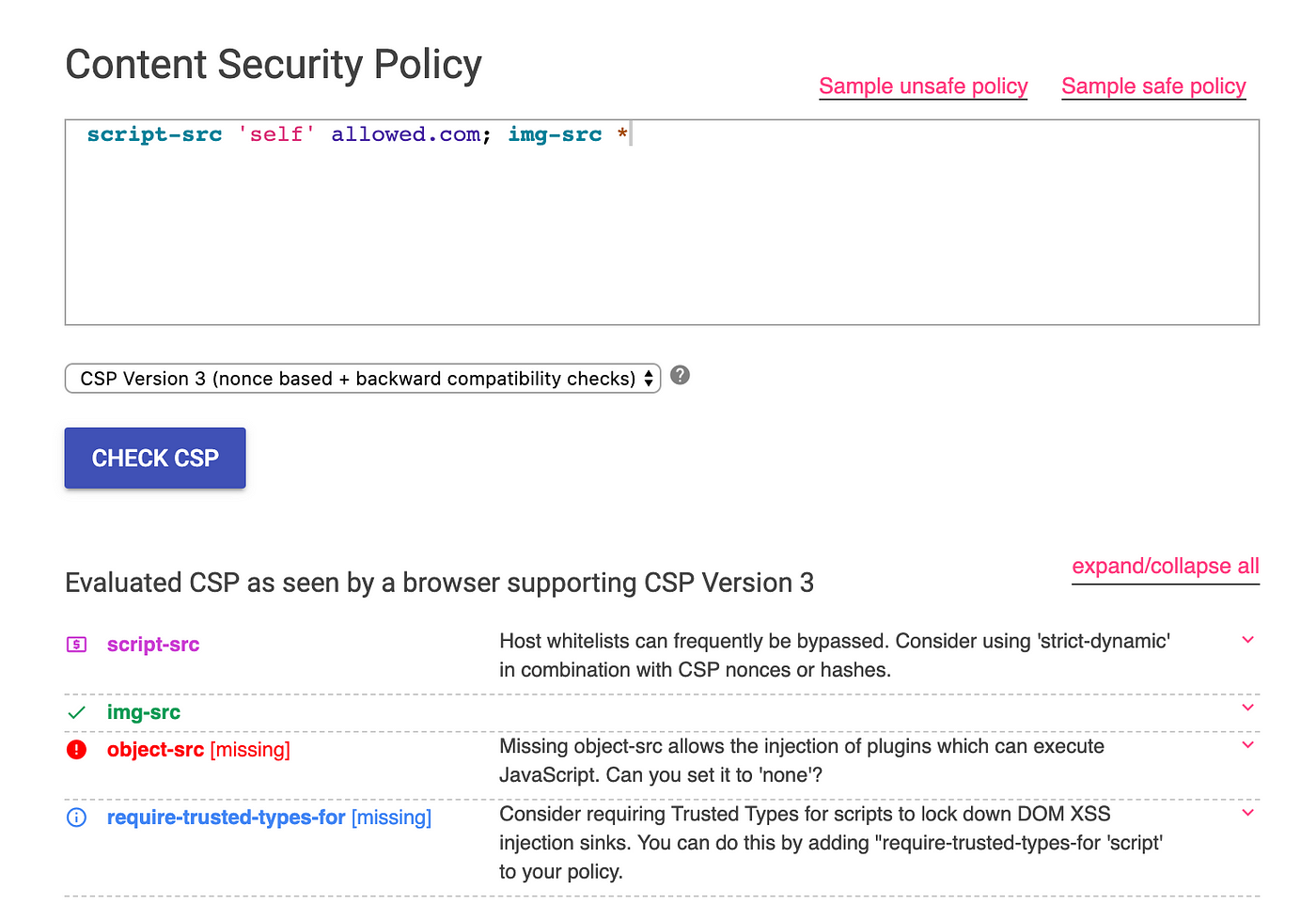
Content Security Bypass Techniques to perform XSS

Analysis of dynamic code updating in Android with security

Cyble — Hydra Android Malware Distributed Via Play Store

Software supply chain threats Software supply chain security
BrainTest - A New Level of Sophistication in Mobile Malware
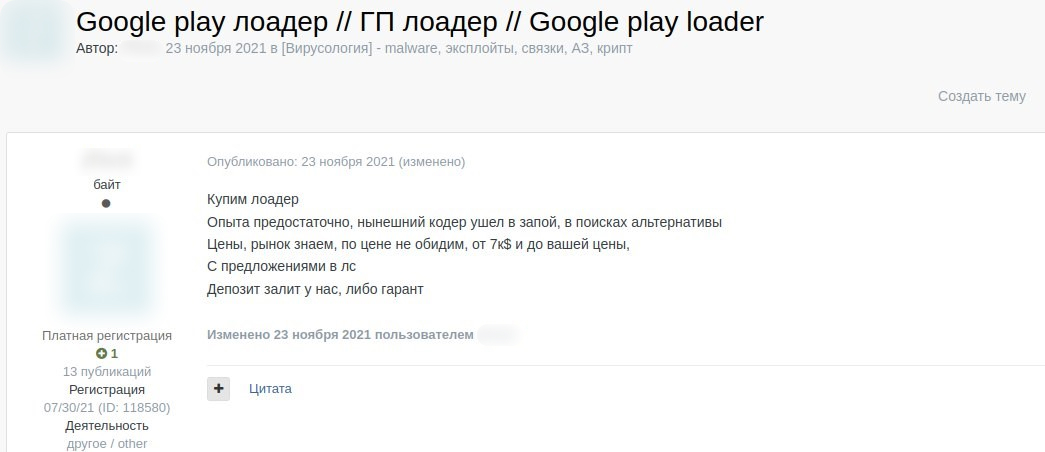
Google Play threat market: overview of dark web offers
de
por adulto (o preço varia de acordo com o tamanho do grupo)