Cybercriminals are circumventing email security with image-based
Por um escritor misterioso
Descrição
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
Security researchers at Inky recently discovered a rash of fraudulent emails that bypass certain conventional spam filters by using image attachments and QR codes. The scams don't
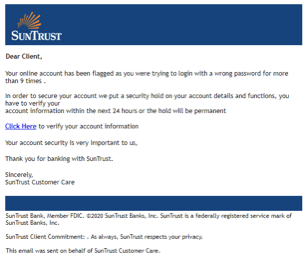
Remote Images Are Pushing Email Filters to Their Limits

Cybercrime - What is, Types and Prevention (Updated)

New Proofpoint Research: How Attackers Exploit People to Circumvent Cyber- security

New Perception Point and Osterman Research Report Shows

Protect Clients, Protect Yourself: Why Advanced Email Security Matters
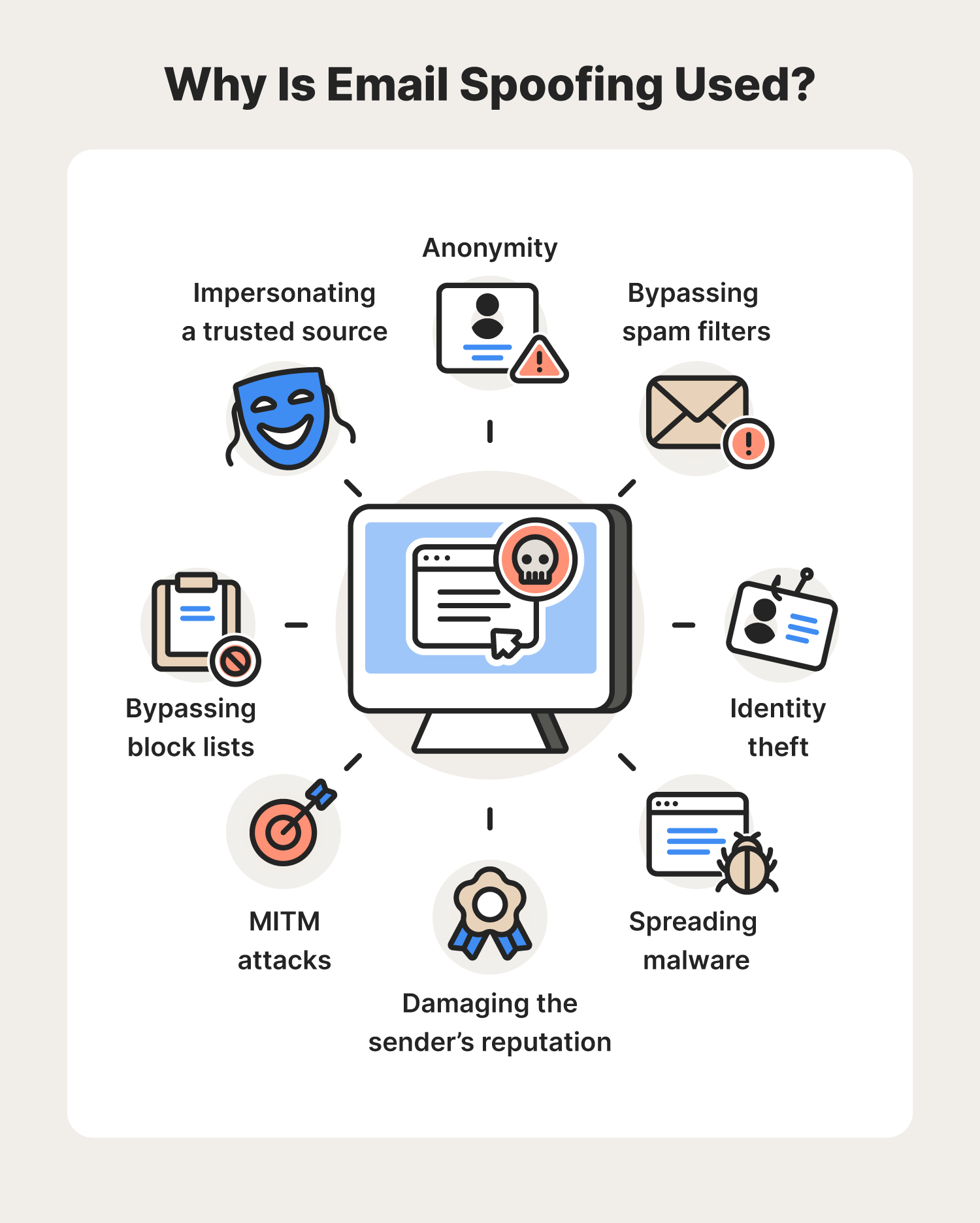
What is email spoofing? A complete guide - Norton

Understanding Phishing Emails: Why They Slip Through Spam Filters

How AI Protects (and Attacks) Your Inbox: The Battle Against Email Threats by Nova Deer Cyber Productions LLC - Issuu

Hackers Are Bypassing Your Email Security Solution & Here's Ho - Guardian Digital .

Effective Strategies for Protecting Against BEC

Four ways cyber-criminals fly under the radar

A Shifting Email Conversation: Email Security is Stuck Looking to the Past
20 Eye-Opening Cybercrime Statistics
de
por adulto (o preço varia de acordo com o tamanho do grupo)