Top 5 Most Common Incident Response Scenarios
Por um escritor misterioso
Descrição
Dealing with cyber threats such as phishing scams, malicious network scanning, and ransomware attacks can be overwhelming. Learn how to protect, detect, and respond to the top five cyber threats.

Top 5 ICS Incident Response Tabletops and How to Run Them

Real Life Examples of Web Vulnerabilities (OWASP Top 10)

Workplace Hazards: Types & Examples
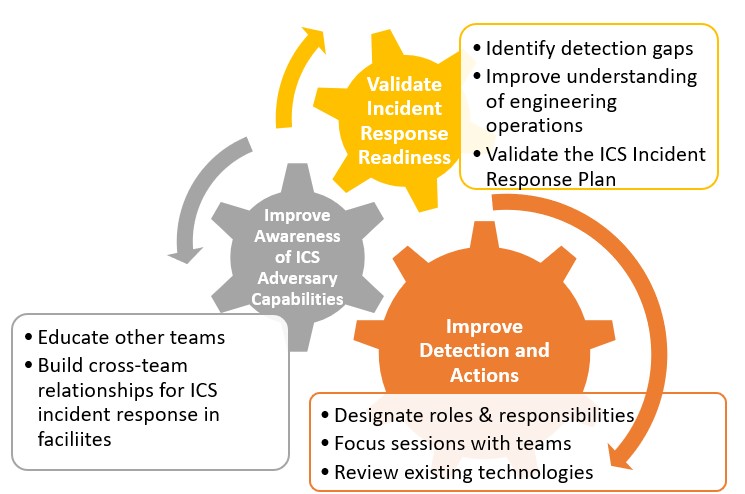
Top 5 ICS Incident Response Tabletops and How to Run Them

SBS CyberSecurity on LinkedIn: Going live tomorrow! Are you interested in exploring the world of…

7 Real-Life Data Breaches Caused by Insider Threats

5 Cyber Incident Response Scenarios to Test on Your Team
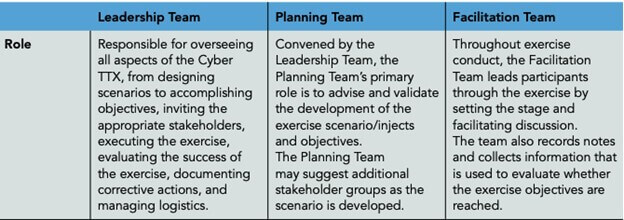
Everything You Need to Know about Cyber Crisis Tabletop Exercises

Six steps for building a robust incident response strategy - IBM

Game‐based learning: A review of tabletop exercises for cybersecurity incident response training - Angafor - 2020 - SECURITY AND PRIVACY - Wiley Online Library

Technical Approaches to Uncovering and Remediating Malicious Activity

Top 5 Incident Response Metrics with Real-World Examples & Impact

5 Industries Most Vulnerable to Cyber Attacks — Data Breaches by Industry
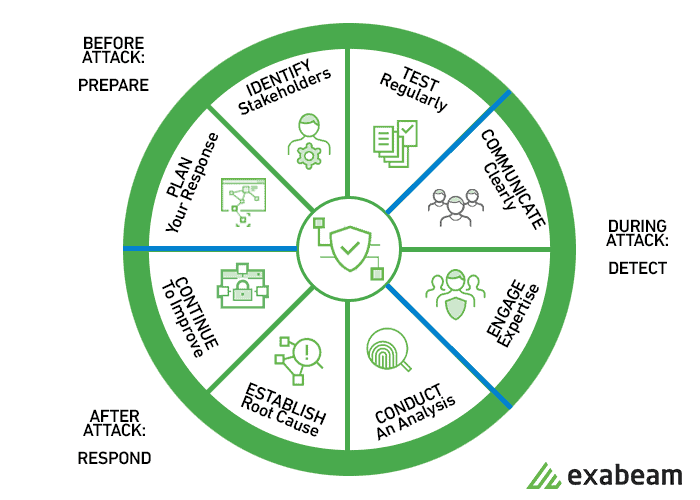
Incident Response Plan 101: How to Build On - Exabeam

9 Common Types of Security Incidents and How to Handle Them — RiskOptics
de
por adulto (o preço varia de acordo com o tamanho do grupo)