PDF) Efficient detection of hacker community based on twitter data
Por um escritor misterioso
Descrição
21 Cybersecurity Twitter Accounts You Should Be Following in 2021 - SentinelOne
Used Book in Good Condition Highlight, take notes, and search in the book

The Practice of Network Security Monitoring: Understanding Incident Detection and Response

Higher Arm Versus Lower Arm Systolic Blood Pressure and Cardiovascular Outcomes: a Meta-Analysis of Individual Participant Data From the INTERPRESS-IPD Collaboration
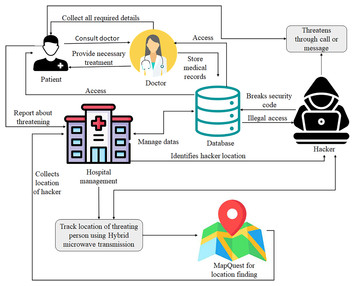
Efficient data transmission on wireless communication through a privacy-enhanced blockchain process [PeerJ]

The CADA-MRIT
Top 10 Cyber Security Projects With Source Code (2023) - InterviewBit

Monitoring Users Opening Malicious Files - Security Spotlight

What Caused the Uber Data Breach in 2022?

Online social networks security and privacy: comprehensive review and analysis

Near-Infrared-II In Vivo Visualization and Quantitative Tracking of Micro/Nanoplastics in Fish

Threat Detection Marketplace - Page 3 of 22 - SOC Prime

ACM: Digital Library: Communications of the ACM
Efficient detection of hacker community based on twitter data using complex networks and machine learning algorithm - IOS Press

Sleight of hand: How China weaponizes software vulnerabilities - Atlantic Council

Building Blocks for Your XDR Journey, Part 2 Why EDR Is the Cornerstone for Great XDR - SentinelOne
de
por adulto (o preço varia de acordo com o tamanho do grupo)