Malware analysis Suspicious activity
Por um escritor misterioso
Descrição
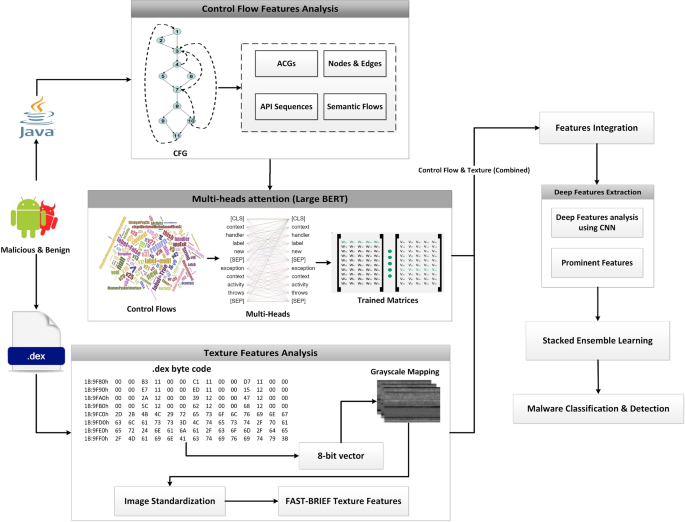
A malware detection system using a hybrid approach of multi-heads

The General Behavior of Ransomware - Cisco Blogs

Malware Analysis Framework v1.0

How to Detect New Threats via Suspicious Activities

1. General Flow of Signature-Based Malware Detection and Analysis
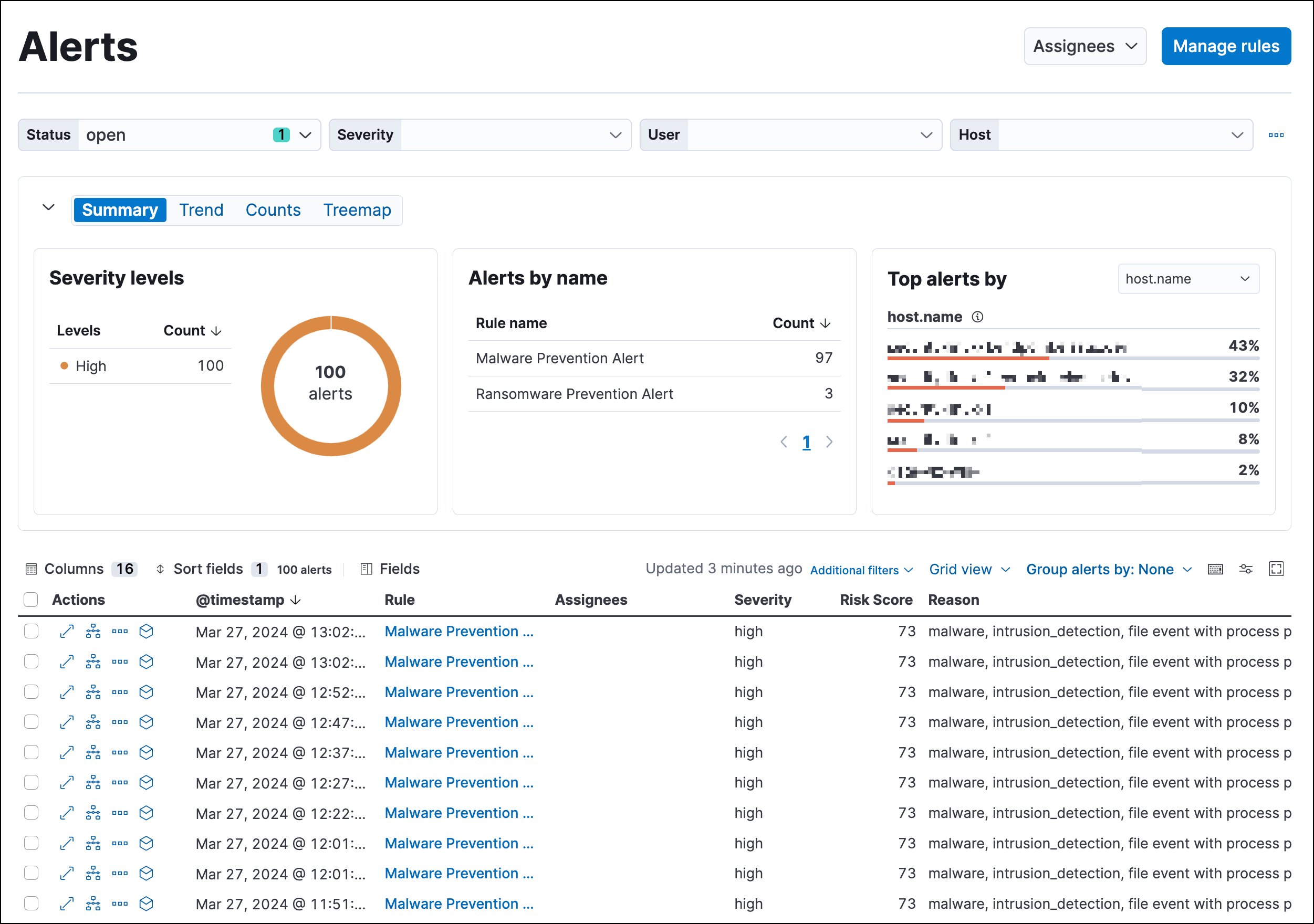
Detections and alerts, Elastic Security Solution [8.11]
Malware analysis cable.exe Suspicious activity

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine
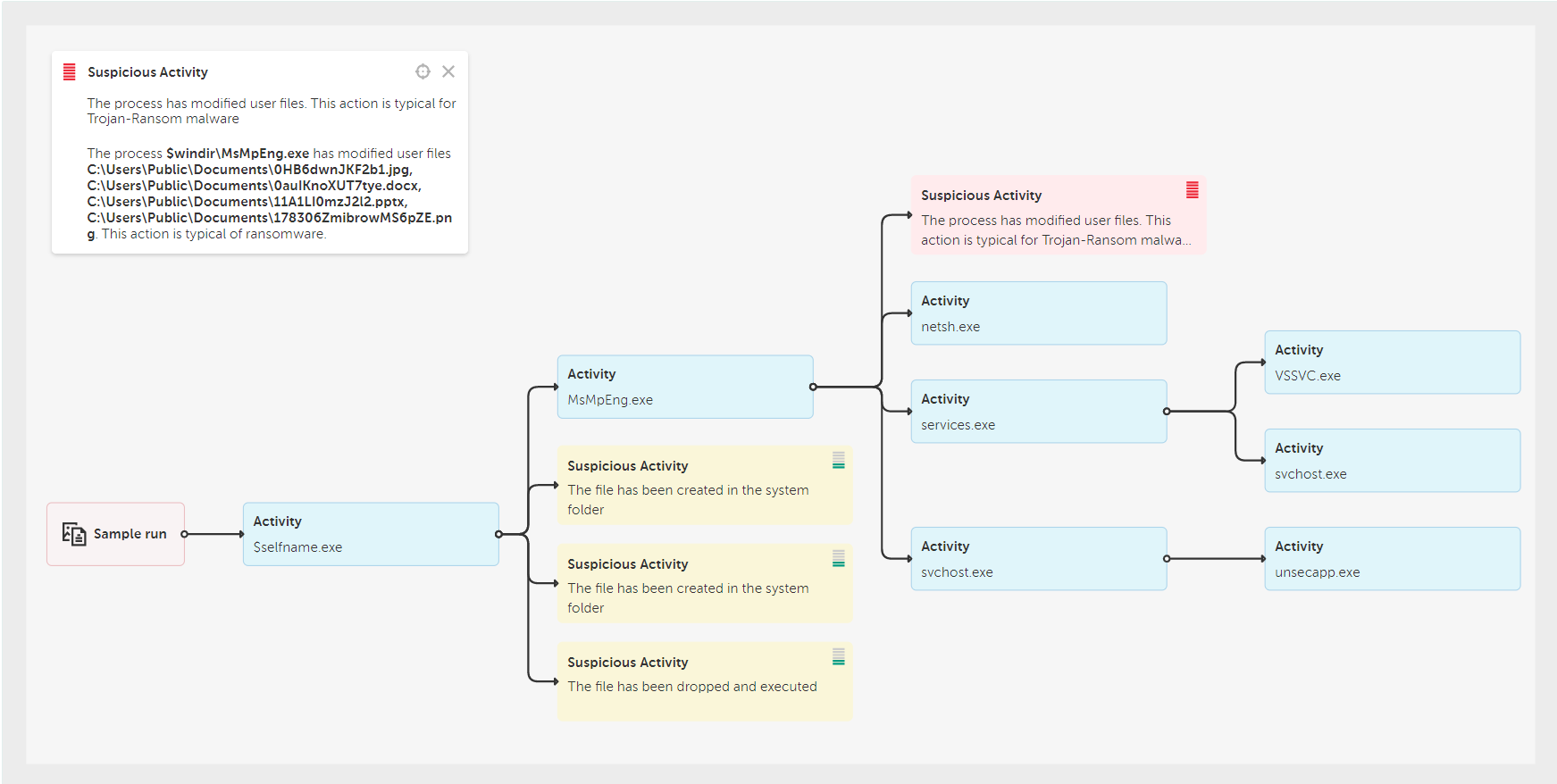
REvil ransomware attack against MSPs and its clients around the

What is Malware Analysis
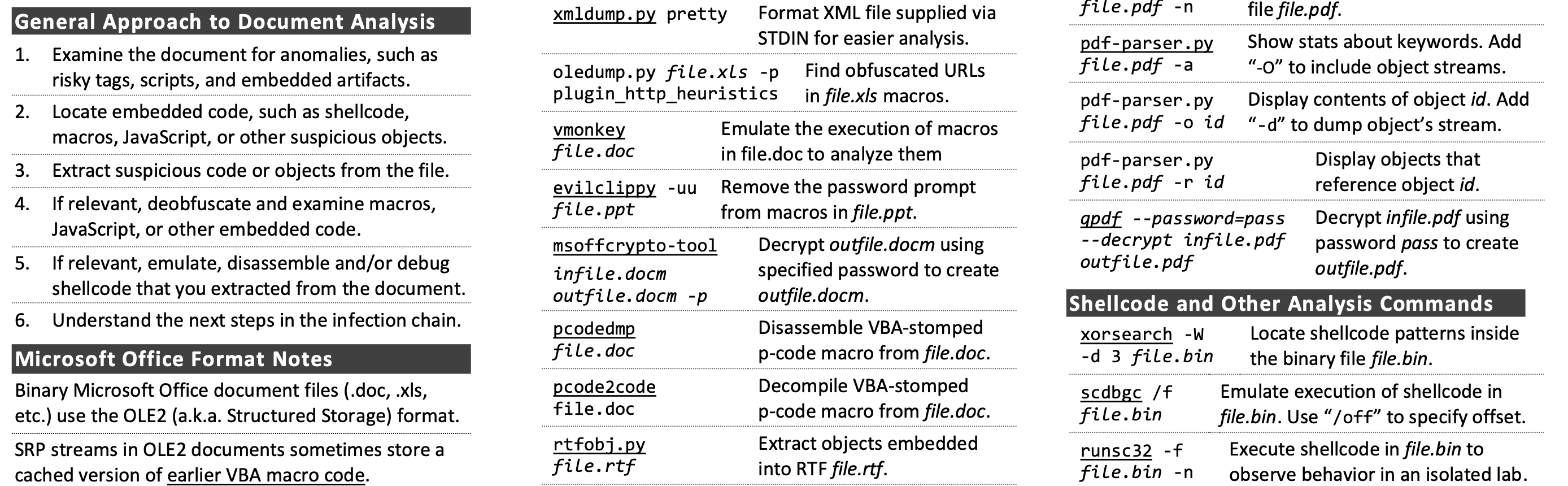
Analyzing Malicious Documents Cheat Sheet
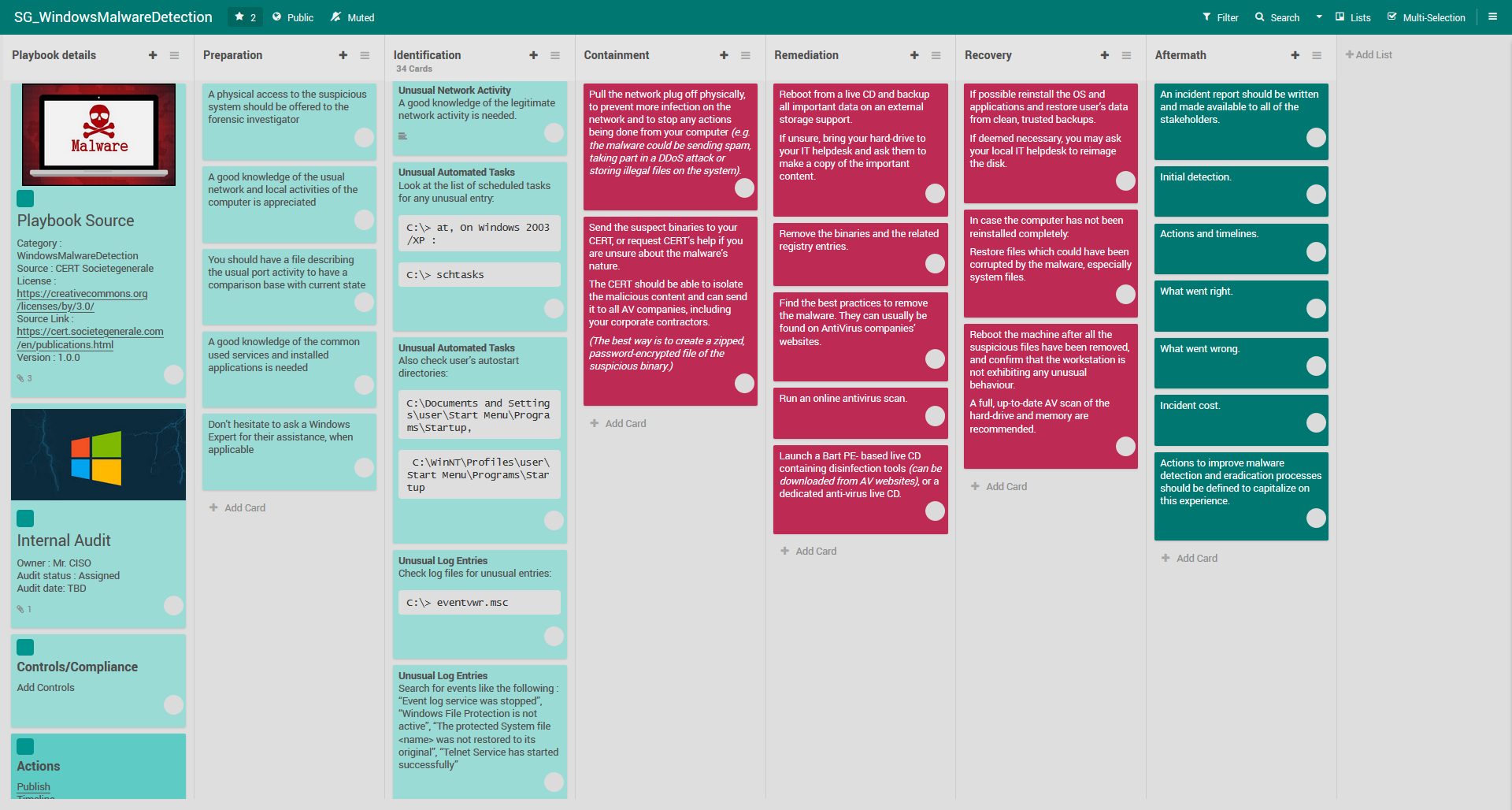
Playbook for Malware outbreak
de
por adulto (o preço varia de acordo com o tamanho do grupo)