Malware analysis Malicious activity
Por um escritor misterioso
Descrição

Malware Analysis: Steps & Examples - CrowdStrike
Malware analysis index.html Malicious activity

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Malware Analysis: Steps & Examples - CrowdStrike

Top 10 Types of Information Security Threats for IT Teams

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Cybersecurity Search Engine

Dynamic malware analysis [34]

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen
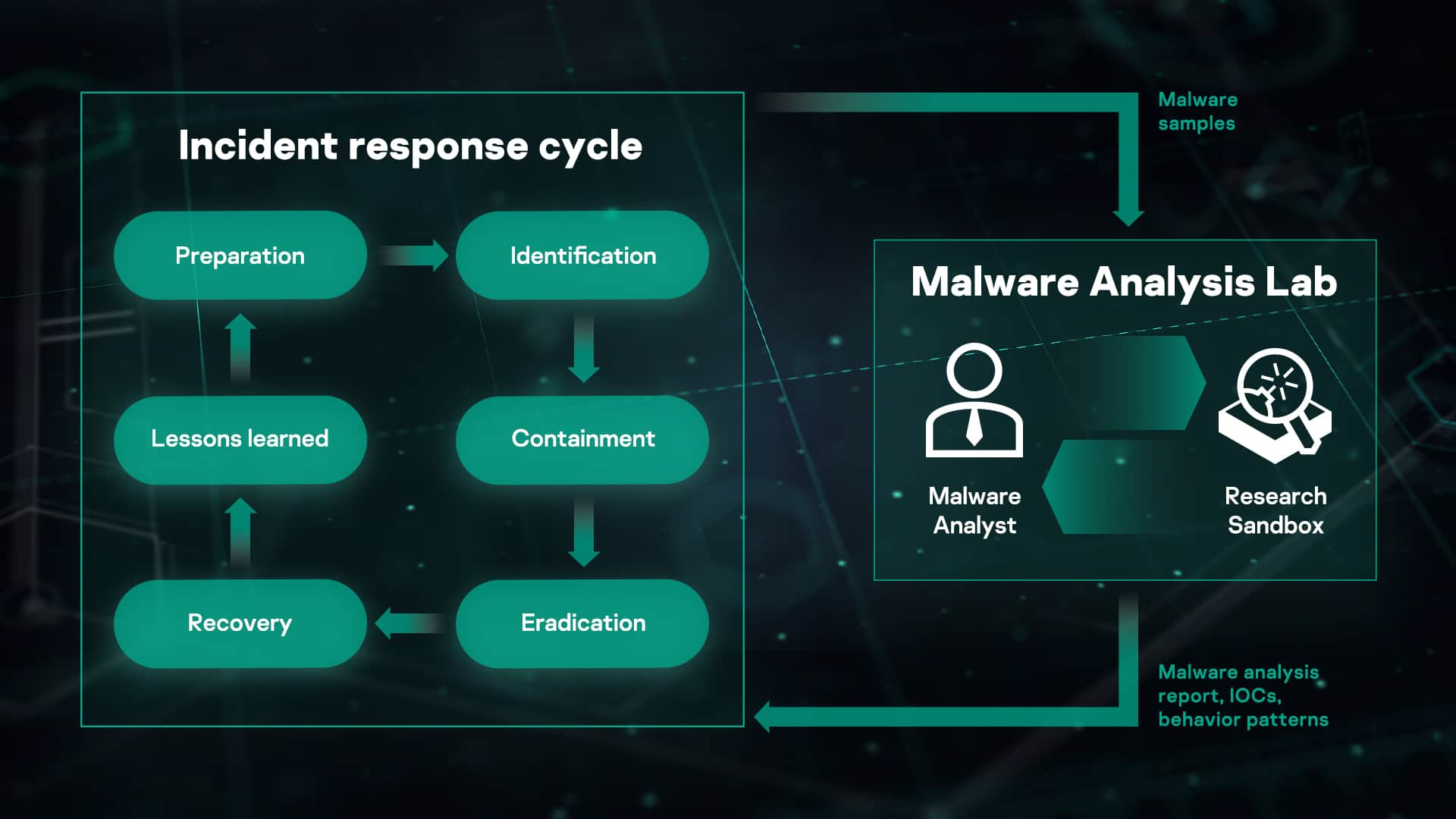
Advanced Automated Malware Analysis – Kaspersky Research Sandbox
de
por adulto (o preço varia de acordo com o tamanho do grupo)





