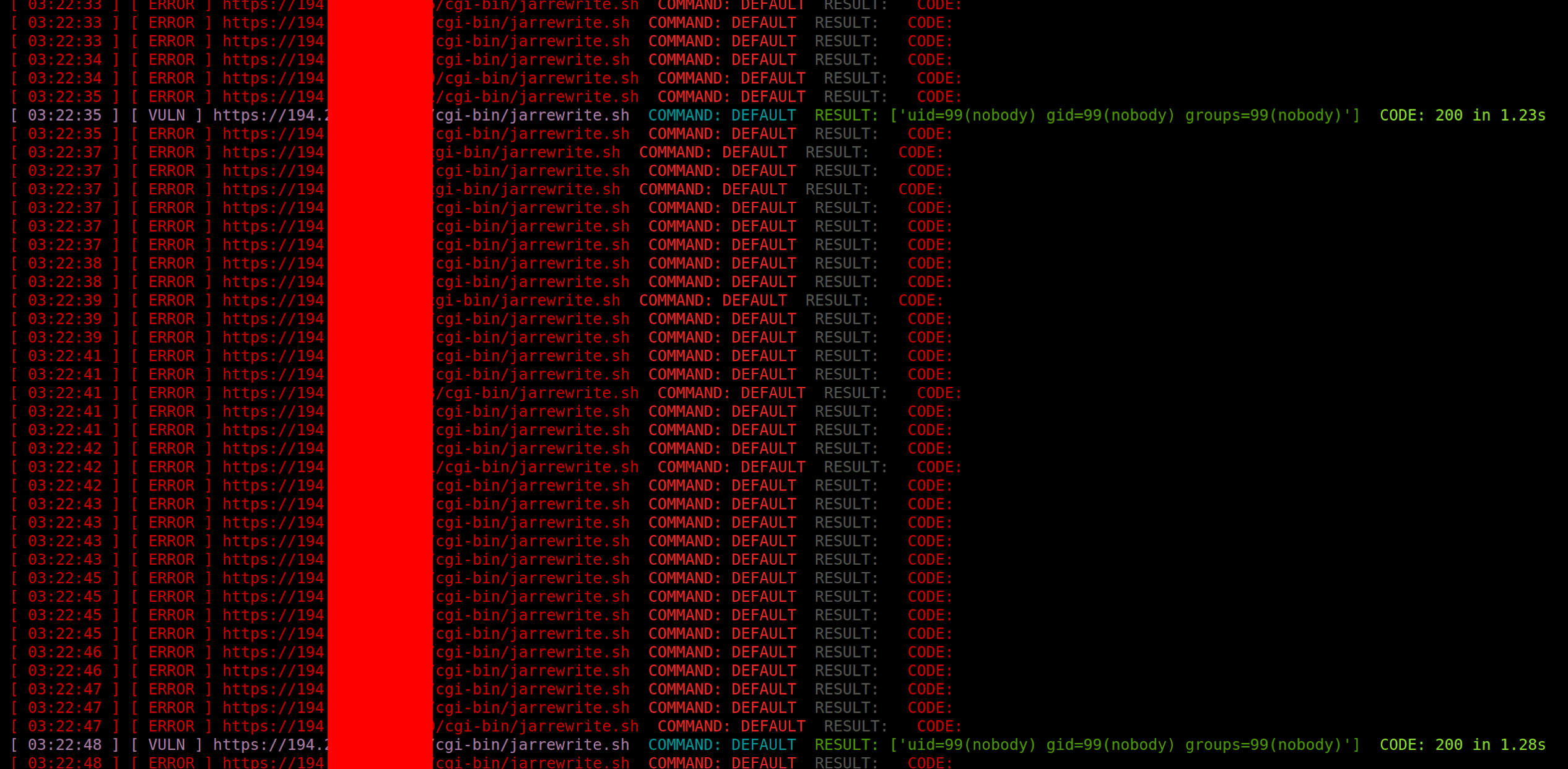
Lab: Blind SSRF with Shellshock exploitation
Por um escritor misterioso
Descrição
This site uses analytics software which fetches the URL specified in the Referer header when a product page is loaded. To solve the lab, use this
Website Hacking Archives - Hackercool Magazine
Website Hacking Archives - Hackercool Magazine

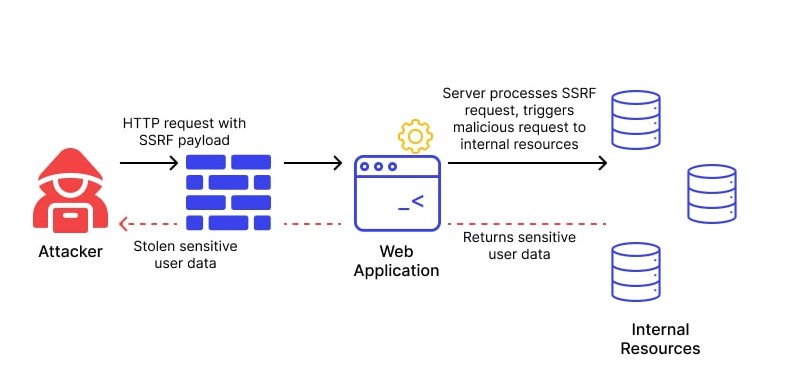
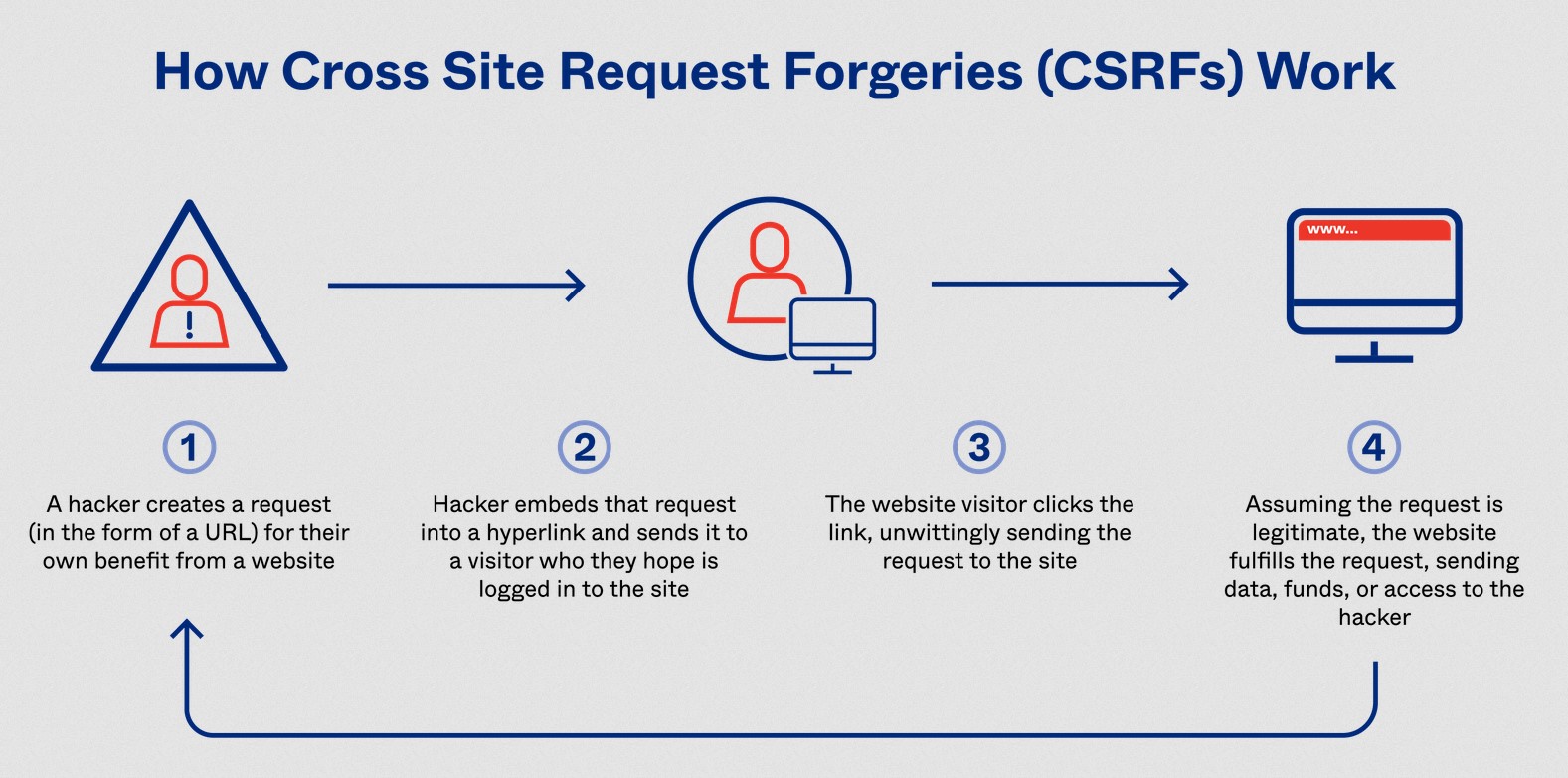
A GUIDE TO SERVER SIDE REQUEST FORGERY(SSRF) » Securityboat

Blind SSRF with Shellshock exploitation (Video Solution)

ABHISHEK KUMAR SINGH on LinkedIn: Lab17: Blind SQL injection with

Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
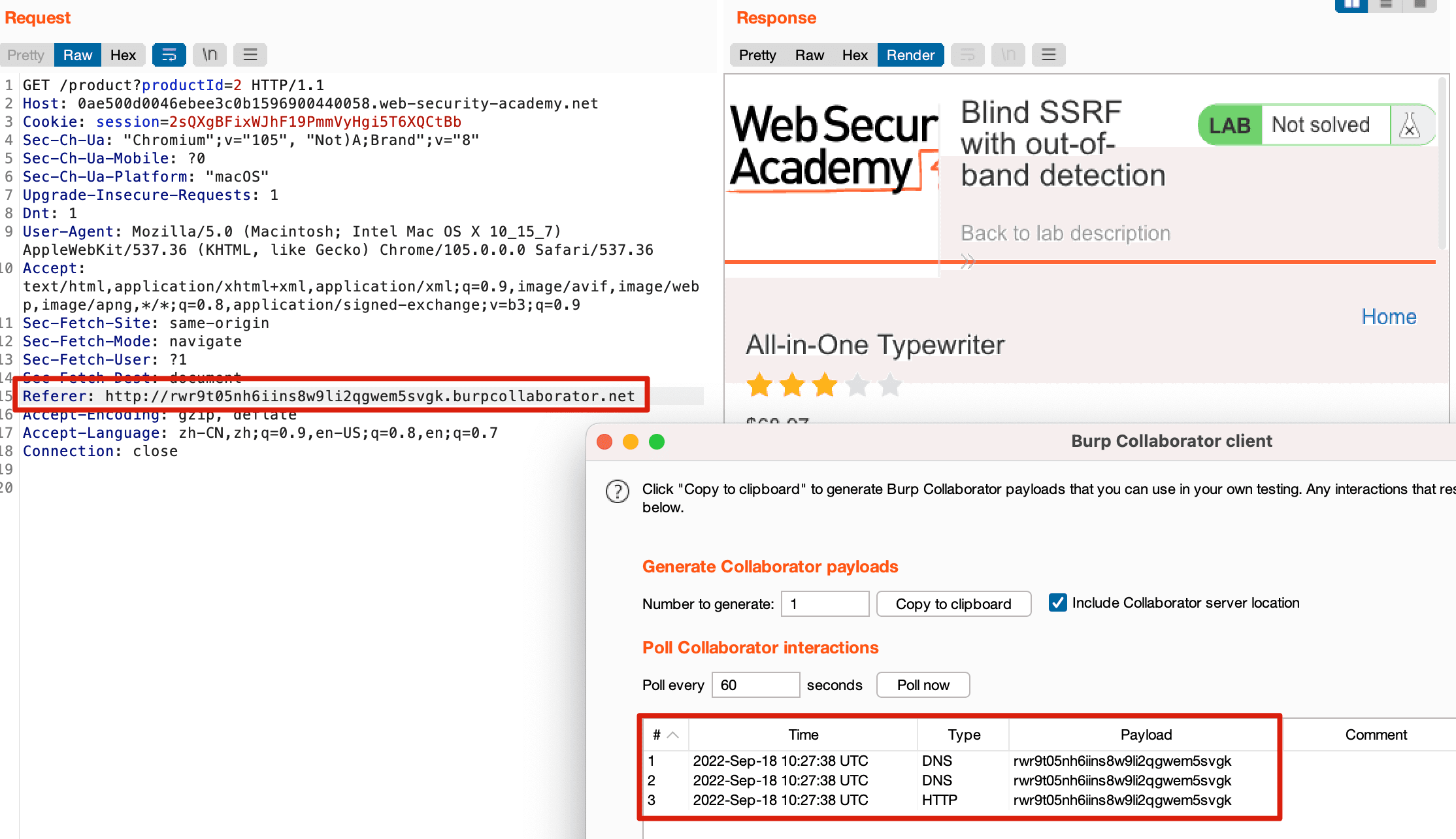
SSRF(服务器跨站请求伪造)基础知识- lca
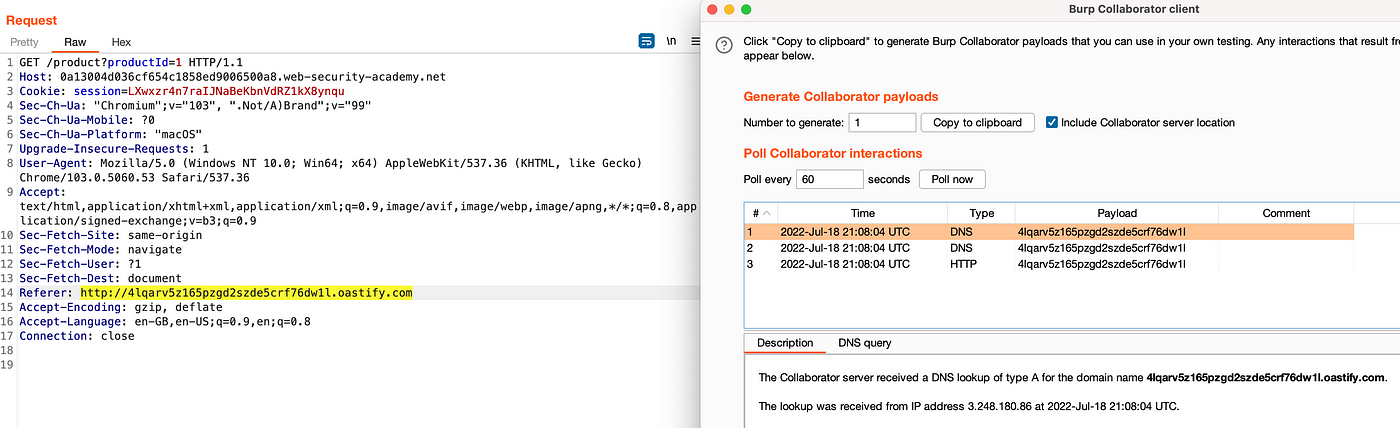
PortSwigger SSRF Labs. Hey all! This write-up is about my…

Exploiting XML-RPC on WordPress that is protected by NGINX : r
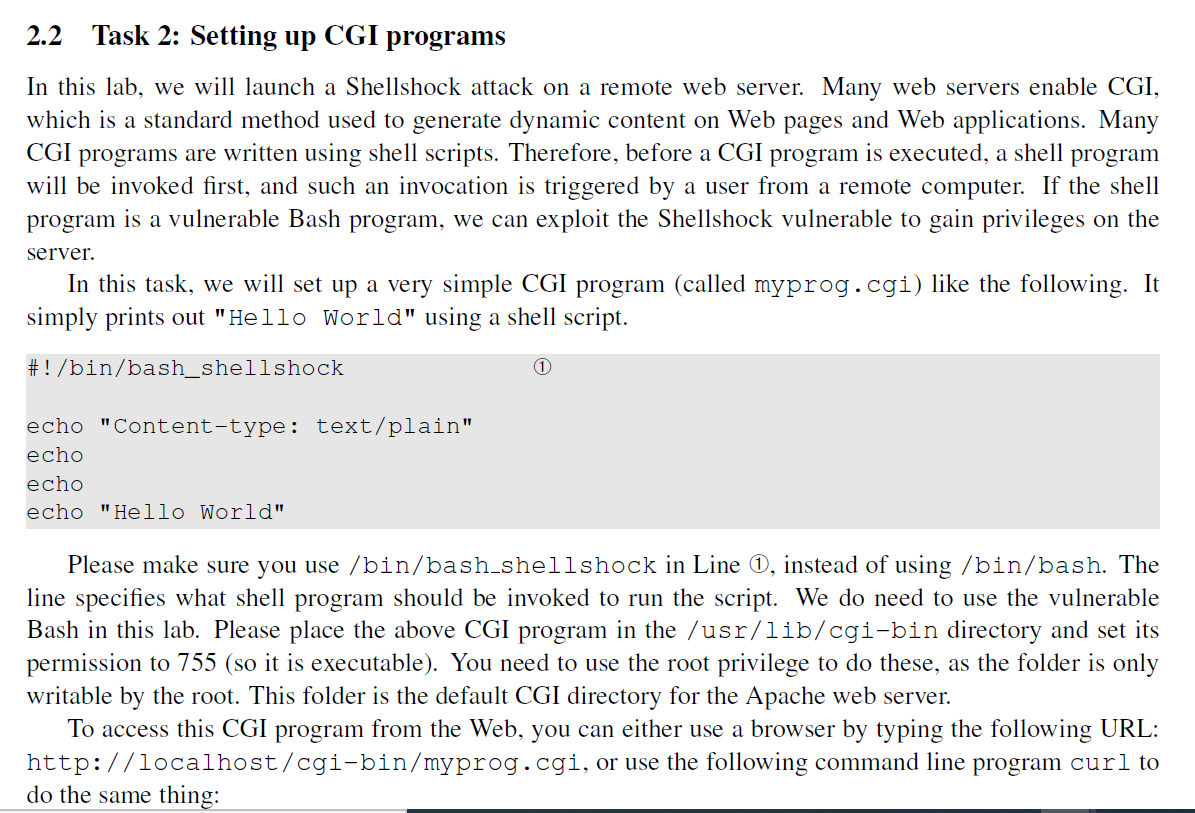
Solved Readings. Detailed coverage of the Shellshock attack

Blind SSRF with Shellshock exploitation (Video solution)

PortSwigger SSRF Labs. Hey all! This write-up is about my…
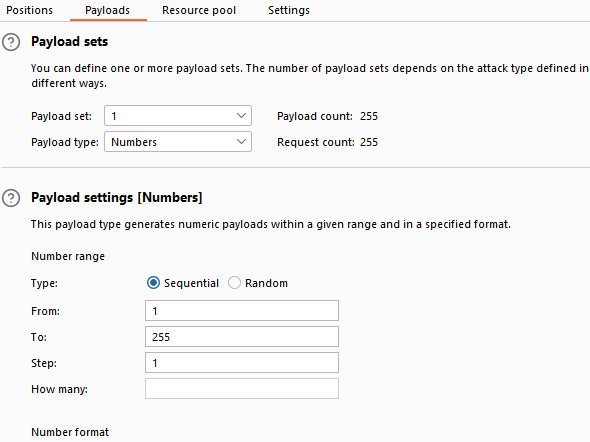
Portswigger Web Security Academy Lab: Blind SSRF with Shellshock
de
por adulto (o preço varia de acordo com o tamanho do grupo)