Information Security: THE CYBER CHESS CLUB - United States Cybersecurity Magazine
Por um escritor misterioso
Descrição
Information security doesn’t start and end with business development experts and implementation specialists. It should have its roots within the foundations of a company, its core concept, and its leadership. Information security practices need to be built into all business processes, including how personnel communicate within the organization and externally with customers, vendors, and competition. Read more
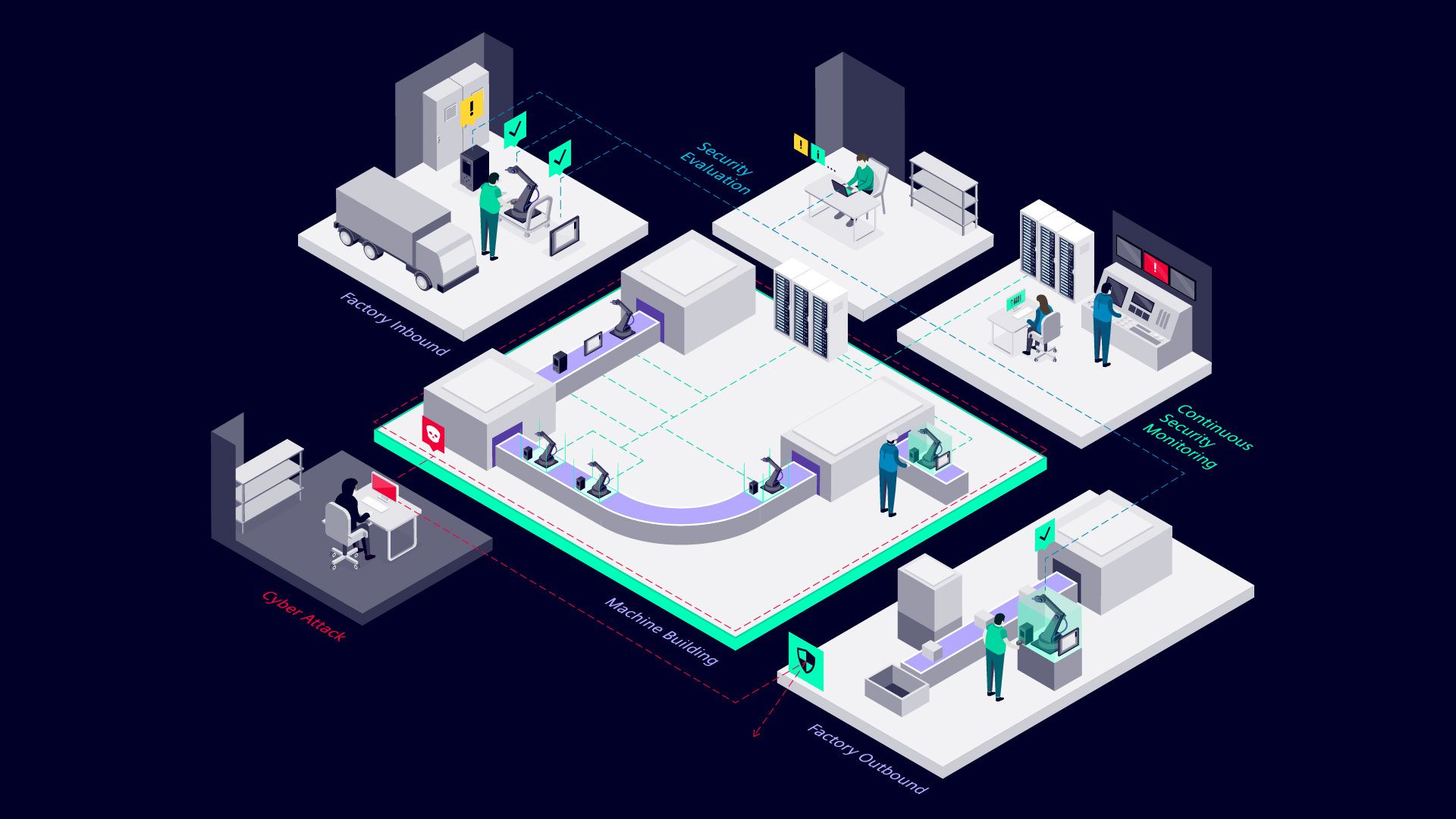
Boosting cybersecurity: Siemens launches new all-in-one security testing suite for industrial networks, Press, Company

Read This Before You Get Hacked Again - United States Cybersecurity Magazine

CHESS: Cyber-security Excellence Hub in Estonia and South Moravia - Red Hat Research

Feature Article Archives - United States Cybersecurity Magazine

Cybersecurity Quarterly (Summer 2023) by Cybersecurity Quarterly - Issuu

Round table: Cybersecurity, the new baby - Business North Carolina

Netwrix Cyber Chief Magazine Your Guide for Cybersecurity
[Evans, Lester] on . *FREE* shipping on qualifying offers. Cybersecurity: An Essential Guide to

Cybersecurity: An Essential Guide to Computer and Cyber Security for Beginners, Including Ethical Hacking, Risk Assessment, Social Engineering, Attack

The Cyber Express #1 Cybersecurity News & Hacker News Site
How does cyber security work? What are its uses? - Quora

Student Organizations

Black Arrow Cyber Consulting — Black Arrow Cyber Threat Intelligence Briefing 17 November 2023

About Us
de
por adulto (o preço varia de acordo com o tamanho do grupo)






