Emerging Defense in Android Kernel
Por um escritor misterioso
Descrição
There was a time that every Linux kernel hacker loves Android. It comes with a kernel from stone-age with merely any exploit mitigation. Writing exploit with any N-day available was just a walk in the
Mobile Threat Defense

Hackers Abuse Loophole in Windows Policy to Load Malicious Kernel Drivers
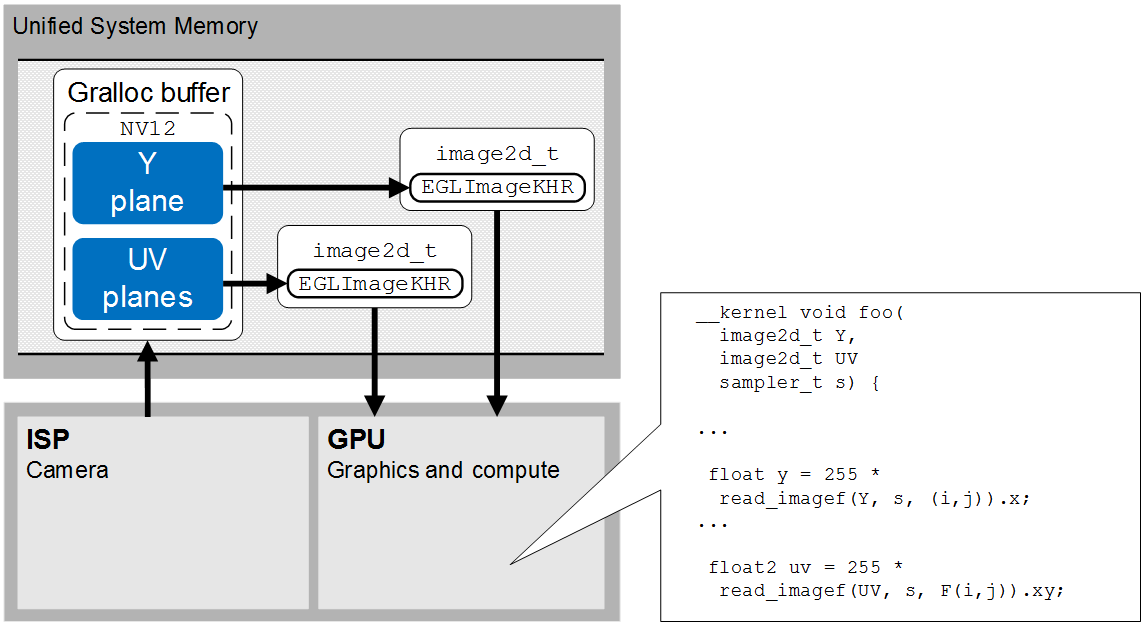
The PowerVR Imaging Framework for Android - Edge AI and Vision Alliance

The Android kernel mitigations obstacle race - The GitHub Blog
GitHub - R0B1NL1N/linux-kernel-exploitation: A bunch of links related to Linux kernel exploitation

Samsung Mobile Solutions Transform How Military Personnel Accomplish Their Missions - Samsung US Newsroom

PDF] A Systematic Study of Elastic Objects in Kernel Exploitation

PDF) A Comprehensive Study of Kernel (Issues and Concepts) in Different Operating Systems

Shining New Light on an Old ROM Vulnerability: Secure Boot Bypass via DCD and CSF Tampering on NXP i.MX Devices, NCC Group Research Blog

PDF] SLAKE: Facilitating Slab Manipulation for Exploiting Vulnerabilities in the Linux Kernel

Android security framework [2].

Sustainability, Free Full-Text
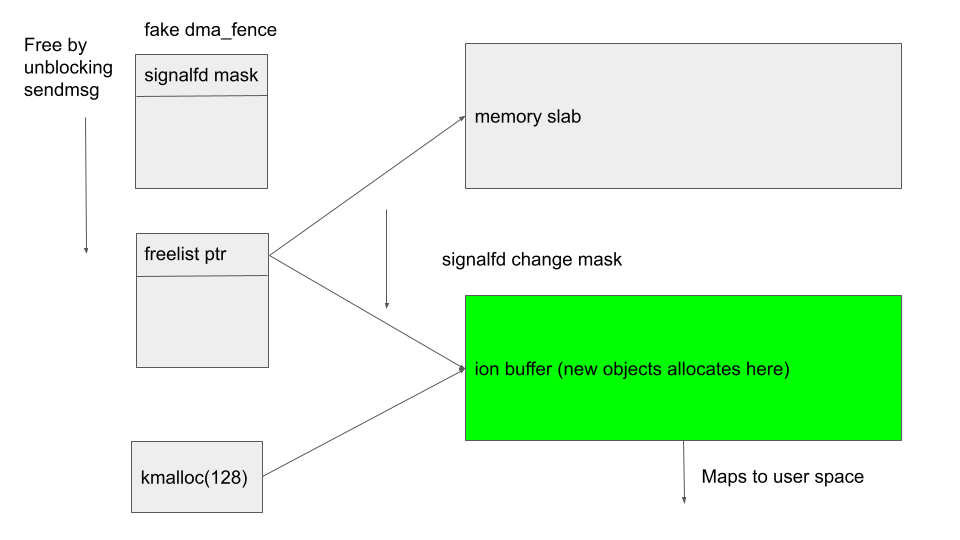
The Android kernel mitigations obstacle race - The GitHub Blog
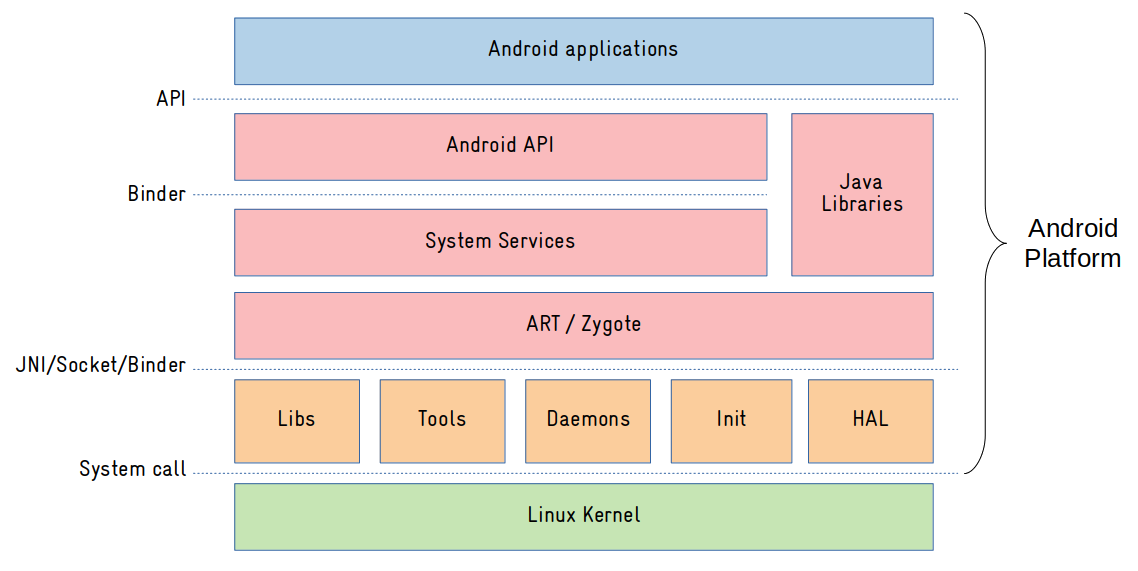
What differs Android from other Linux based systems?
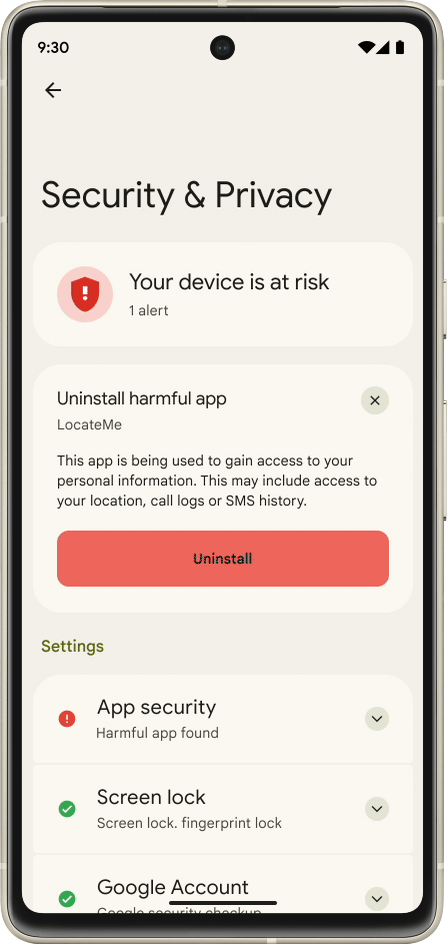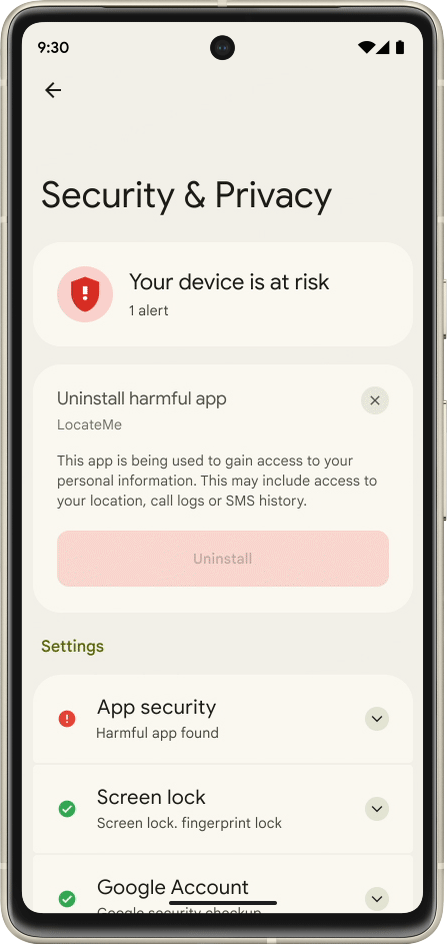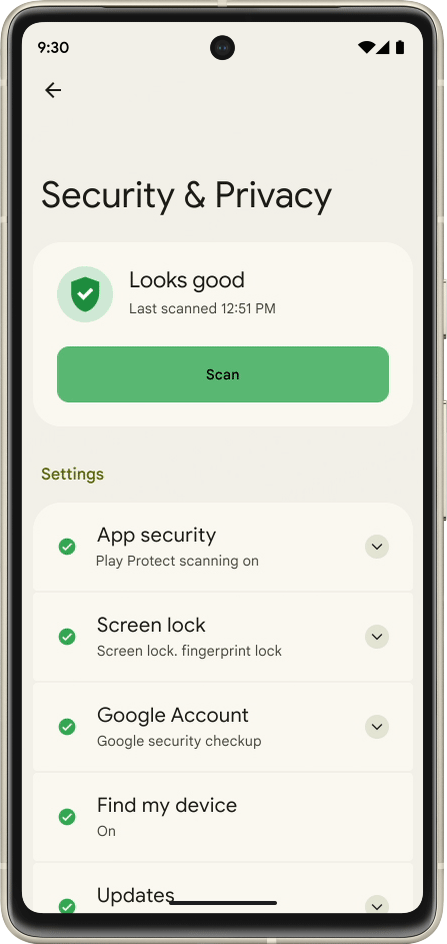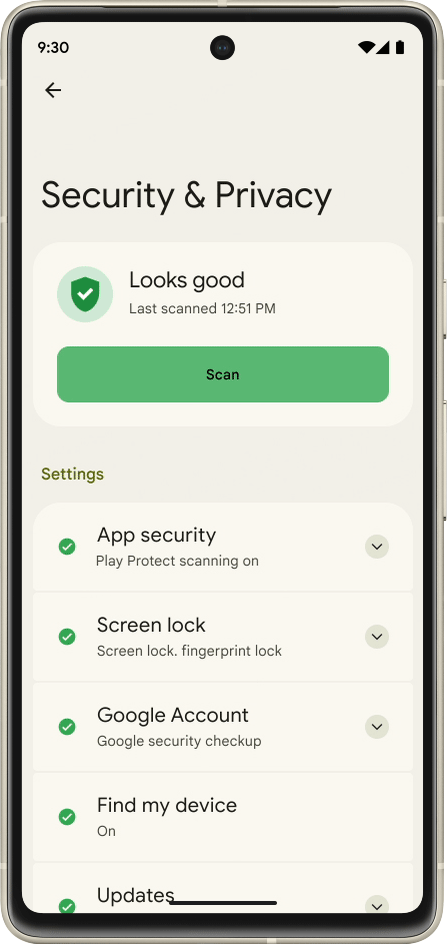
Google Online Security Blog: 2022
de
por adulto (o preço varia de acordo com o tamanho do grupo)




:strip_icc()/i.s3.glbimg.com/v1/AUTH_cf9d035bf26b4646b105bd958f32089d/internal_photos/bs/2020/s/w/127f6pRz6kmb16yN2QEg/2016-10-26-780-crosser-150-ed-6.jpg)
)
