Complete UAF exploit - UD Capture
Por um escritor misterioso
Descrição

Estimating the Bit Security of Pairing-Friendly Curves

Use-After-Use-After-Free Exploit UAF by Genrating Your Own
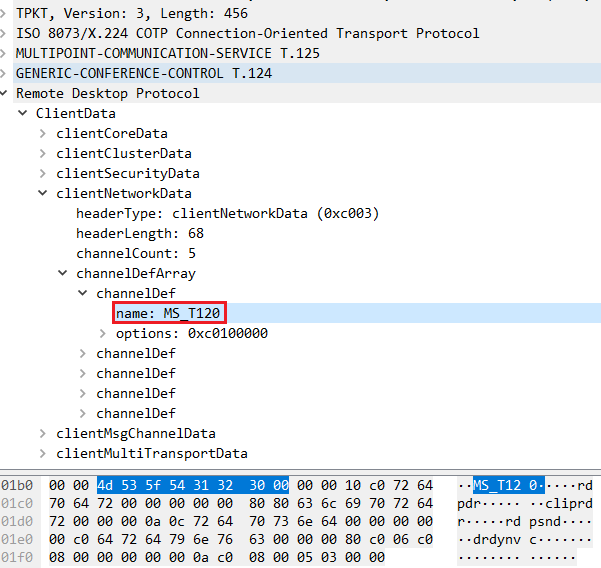
Exploitation of Windows RDP Vulnerability CVE-2019-0708 (BlueKeep)

Reverse Engineering Coin Hunt World's Binary Protocol

Automated Use-After-Free Detection and Exploit Mitigation: How Far

Automated Use-After-Free Detection and Exploit Mitigation: How Far
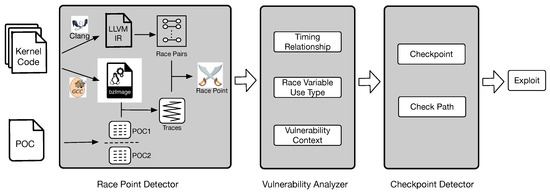
Applied Sciences, Free Full-Text
Complete UAF exploit - UD Capture

Automated Use-After-Free Detection and Exploit Mitigation: How Far
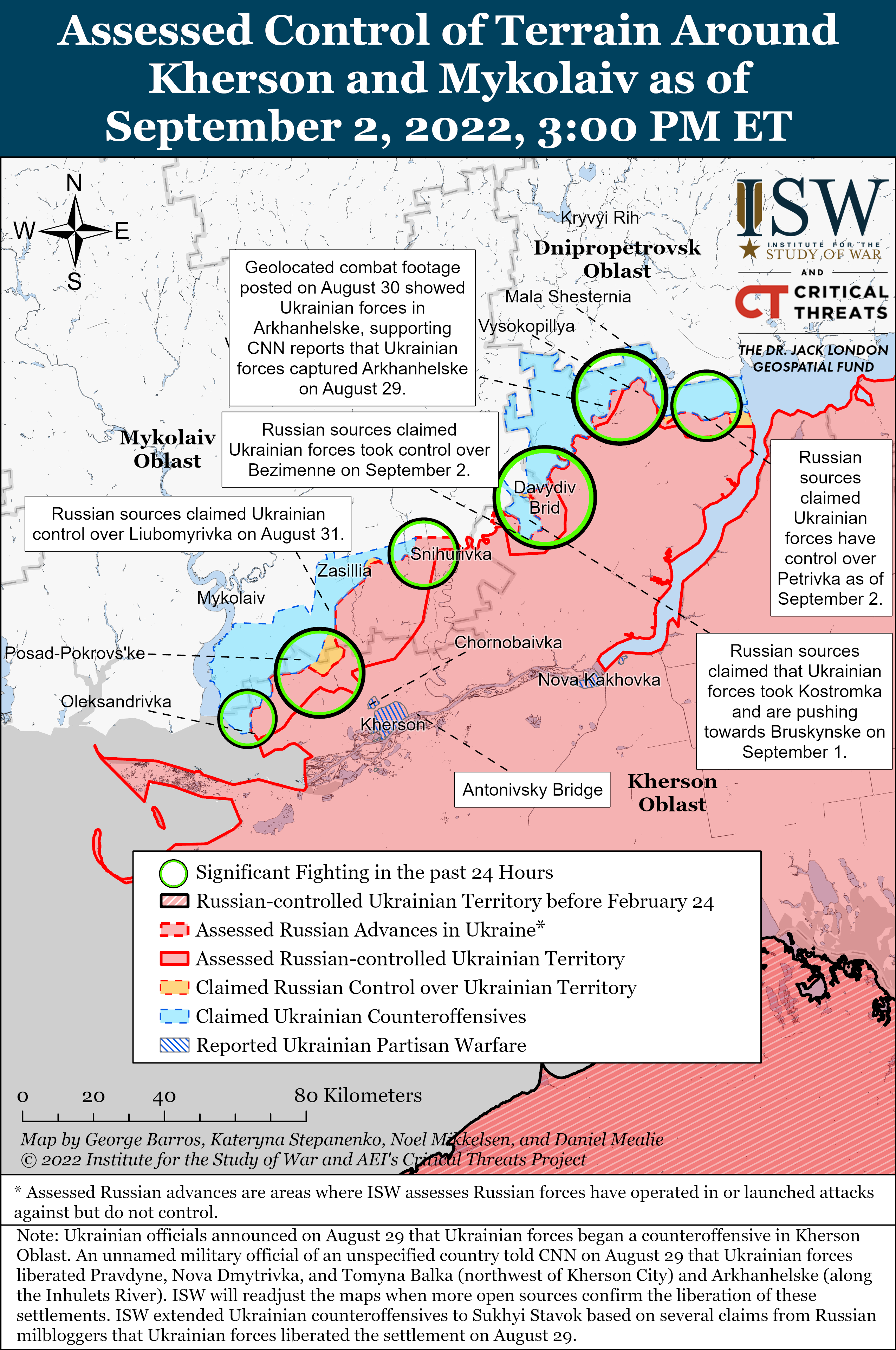
General David H. Petraeus, US Army (Ret.) on LinkedIn
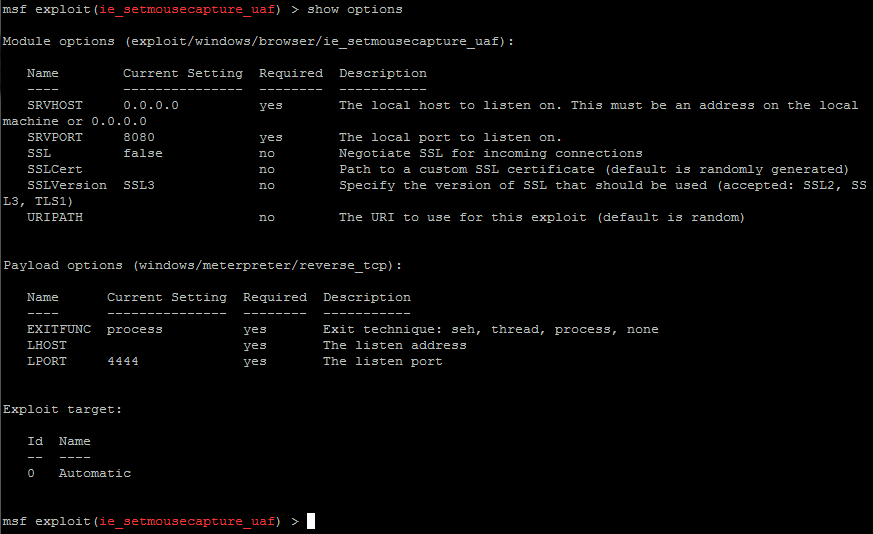
Blog for and by my students, current and future: Exploiting and

A fine-grained classification and security analysis of web-based
de
por adulto (o preço varia de acordo com o tamanho do grupo)